
Introduction
Cyberattacks targeting the energy sector are increasing, driven by a host of geopolitical and technological factors. A report published by Sophos in July 2024, and which surveyed 275 cybersecurity and IT leaders from the energy, oil/gas, and utilities sector across 14 countries, found 67% of respondents who said their organizations had suffered a ransomware attack in the last year.
While Sophos’ figure remained steady year-over-year, a January 2025 report authored by TrustWave said that ransomware attacks targeting the energy and utilities sectors increased by 80% in 2024 compared to the previous year. Most of these breaches have only managed to compromise IT environments, as opposed to more critical operational technology (OT) networks, but the threat to the latter is rapidly intensifying.
Moreover, ransomware is just one aspect of the broader energy-sector threat landscape. This threat intelligence research is a continuation of our material published last year - "Ransomware Attacks against the Energy Sector on the rise - Nuclear and Oil & Gas are Major Targets in 2024", highlighting threat actors targeting energy installations in North America, Asia, and the European Union, including nuclear facilities and related research entities.
Hacktivism is another prevailing threat targeting energy firms, with ideologically motivated adversaries linked to Russia and various Gaza-nexus adversary groups attempting to build credibility by publicizing alleged compromises of various victims’ OT networks. Most concerning, nation-state espionage actors linked to China, Iran, and North Korea have also increasingly been observed targeting the energy sector, including nuclear facility personnel.
These cyber-espionage campaigns are primarily driven by geopolitical considerations, as tensions shaped by the Russo-Ukraine war, the Gaza conflict, and the U.S.’ “great power struggle” with China are projected into cyberspace. With hostilities rising, potentially edging toward a third world war, rival nations are attempting to demonstrate their cyber-military capabilities by penetrating Western and Western-allied critical infrastructure networks. Fortunately, these nation-state campaigns have overwhelmingly been limited to espionage, as opposed to Stuxnet-style attacks intended to cause harm in the physical realm.
A secondary driver of increasing cyberattacks against energy targets is technological transformation, marked by cloud adoption, which has largely mediated the growing convergence of IT and OT networks. OT-IT convergence across critical infrastructure sectors has thus made networked industrial Internet of Things (IIoT) appliances and systems more penetrable to threat actors. Specifically, researchers have observed that adversaries are using compromised IT environments as staging points to move laterally into OT networks.
Compromising OT can be particularly lucrative for ransomware actors, because this type of attack enables adversaries to physically paralyze energy production operations, empowering them with the leverage needed to command higher ransom sums. In cyber-military or cyber-terroristic scenarios, however, the sabotage of OT systems can be catastrophic for physical environments and human life.
Another technological trend that has transformed the threat environment for energy firms is rapidly advancing AI adoption. Not only has AI lowered the barriers to entry for certain types of attack campaigns, but the growing integration of AI with energy sector networks has introduced a maelstrom of new cyber-risk scenarios.
This trend has most notably impacted the nuclear sector, with Constellation Energy, the largest nuclear energy conglomerate in North America, announcing in 2022 that they were “looking at AI to decrease our customers’ energy costs and to optimize the many tasks they perform on a regular basis.” At the same time, recent announcements from AI and cloud-focused Big Tech firms like Microsoft, Meta, and Google indicate that they have plans to tap nuclear energy to power their future data centers.
Beyond the emerging nuclear-AI nexus, the North American Electric Reliability Corporation (NERC), a non-profit international regulatory authority that enforces industry standards in the U.S. and Canada, warned last year that American power grids are becoming increasingly vulnerable to cyberattacks. According to NERC, the number of susceptible points in electrical networks is growing by about 60 per day.
A Reuters report on NERC’s warning noted that “geopolitical conflict, including Russia's invasion of Ukraine and the war in Gaza, have dramatically increased the number of cyber threats to North American power grids.” Resecurity’s second report on cyber threats targeting energy operators will detail recent Dark Web activity, highlighting adversary claims of successful breaches impacting this critical infrastructure sector.
The report will present findings collected by Resecurity’s HUNTER threat intelligence unit in order of ransomware-related incidents, access brokers, hacktivist leaks, and breaches specifically targeting the nuclear sector.
Ransomware-Nexus Leaks
The most significant energy-sector ransomware attack of the last year was RansomHub’s breach of Halliburton in August 2024. Headquartered in Dubai (UAE) and Houston (USA), Halliburton is the world’s second-largest oil service company and is involved in most of the world’s fracking operations. According to BleepingComputer, the RansomHub attack cost Halliburton $35 million in losses “after the breach caused the company to shut down IT systems and disconnect customers.”
In April 2025, HUNTER analysts observed an announcement on the RAMP cybercrime forum indicating that RansomHub has decided to move to DrangForce’s ransomware-as-a-service (RaaS) infrastructure.

In February 2025, Resecurity published a report documenting DragonForce’s recent targeting of Saudi Arabia. The budding partnership between these groups is an intriguing development in the RaaS ecosystem, particularly given their strong reputation and popularity among more accomplished ransomware actors and the recent disbandment of elite threat actor group BlackBasta.
Notably, DragonForce also claimed responsibility for a December 2024 data breach that impacted Luxembourg-based renewable energy investment firm Ikav Energy. According to the company’s webpage, “IKAV is an international asset management group that provides institutional investors with investment solutions spanning a broad range of infrastructure energy assets, including solar, concentrated solar power, wind, energy efficiency, geothermal, thermal power plants and upstream.”
This attack resulted in the compromise of nearly 177 GB of IKAV data, according to DragonForce’s December shame-blog posting. In March, Comparitech reported that Ikav “notified 722 people in Texas and 15 in Massachusetts of the breach, with more victims expected as more states disclose their own breach figures.” Data compromised in this attack included Americans’ names and social security numbers (SSNs), according to Comparitech.
While this ransomware attack did not directly target an energy sector firm, the breach highlights the leading role of supply-chain and third-party risks to energy sector firms, a pervasive theme that Resecurity will expound upon throughout this report.
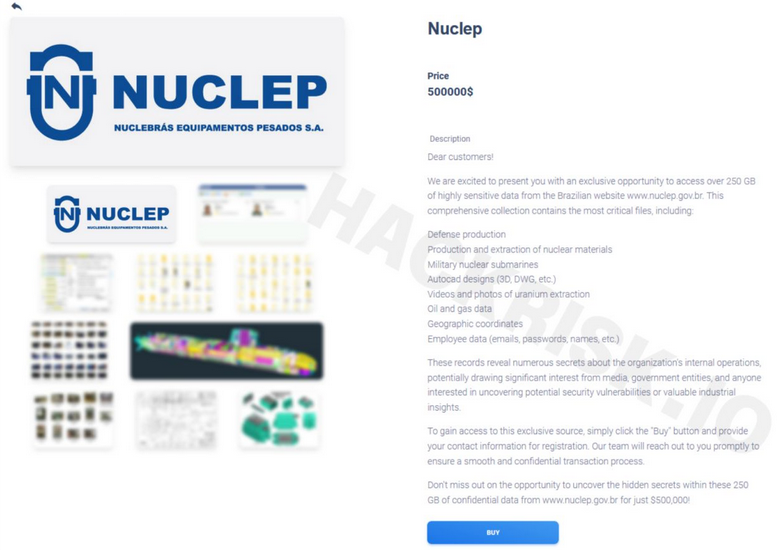
There were several independent ransomware operators identified, such as the "spin-off" of Babuk Ransomware, which is now under the management of new owners. The group has targeted Nuclebrás Equipamentos Pesados S.A., commonly shortened to NUCLEP, a Brazilian state-owned nuclear company specialized in nuclear engineering. In fact, the stolen data for sale, presumably exfiltrated from this victim organization, was offered for sale almost eight months ago by another ransomware group known as 'Meow' or 'Meow Leaks'. Notably, the new spin-off of the prominent ransomware group has leaked several exclusive files that were not previously available at 'Meow Leaks,' which may add to their credibility. At the same time, there is a significant difference in the volume of data offered for sale. The original 'Meow Leaks' included only 250 GB of data, while the actors calling themselves 'Babuk' are offering 1.7 TB, which could be misleading. Likely, these actors were familiar with the root cause of the original leak and could interact with the access broker responsible for unauthorized access. Considering the specifics of work surrounding such enterprises, cybercriminals aim to profit from sensitive R&D; that's why they set an extremely high price amplified by speculative narratives.

The actors had an ambitious plan to extort the victim organization and demanded over $500,000 as ransom payment. They also offered an option for exclusive acquisition for $1.5 million. It is not clear if they were successful in receiving any payment, but the data had been removed along with their DLS for some time before later emerging again under the new brand of Babuk. In fact, Resecurity does not connect this reincarnation with the original Babuk Ransomware, but the actors are capitalizing on their brand in the underground world.
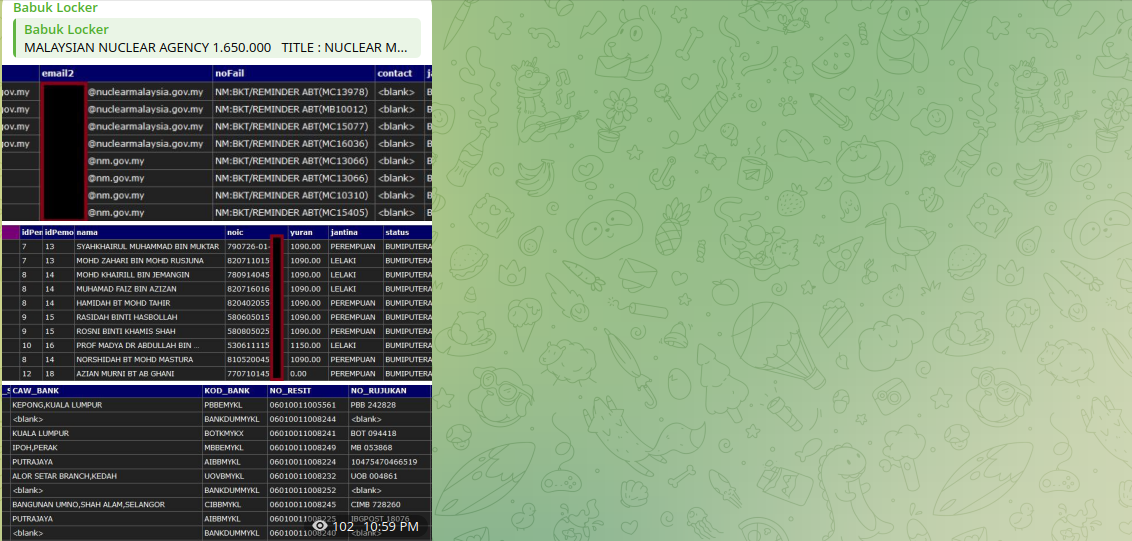
Notably, the same group attempted to extort the Malaysian Nuclear Energy Agency in the past. Samples of stolen data, including employee records, have been published on a Telegram channel and Pastebin. In fact, the initial access to this victim was offered for sale earlier on the Dark Web just for $5,000 (described in the next sections of this report).
But in terms of ransomware-related energy data leak activity, the most prolific threat actor groups observed by HUNTER over the last six months are Cl0P and HellCat. While Cl0P is believed to be a Russia-nexus ransomware collective, HellCat appears to be comprised of multiple native English-speaking members, the most prominent being ‘Pryx’ and ‘Rey.’
Over the last five months, an access broker many researchers presumed to be associated with Cl0P, and who goes by the aliases ‘AntiBrok3rs’ and ‘Nam3L3ss,’ has leaked data from at least 15 energy sector victims that were initially compromised by the ransomware gang’s 2023 MOVEit supply-chain attack. The threat actor posted these data leaks on Breach Forums.
However, AntiBrok3rs publicly denied any affiliation with Cl0P in a December 2024 Breach Forums post titled “Putting cl0p ties to bed for good.”
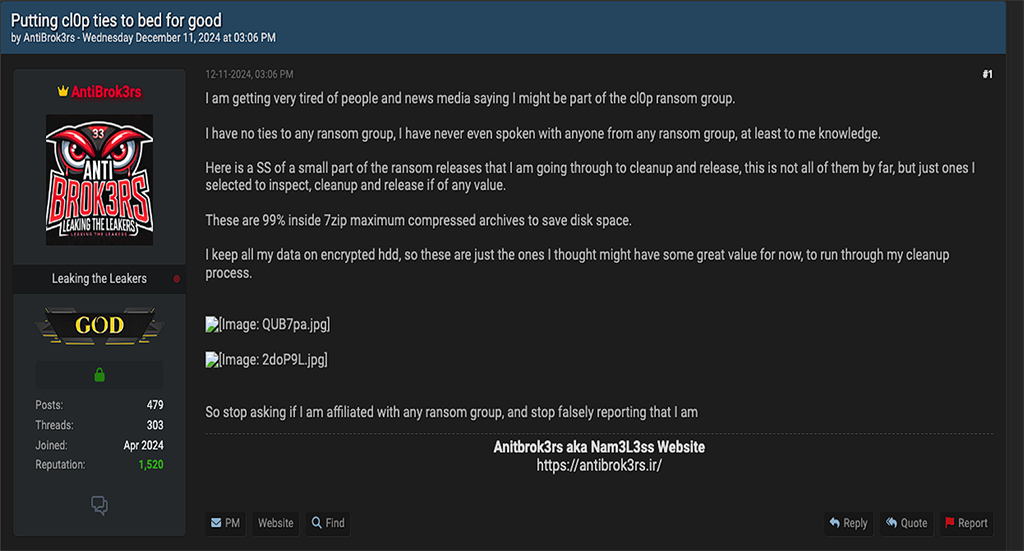
In the post, AntiBrok3rs writes “I have no ties to any ransom group, I have never even spoken with anyone from any ransom group, at least to me knowledge.” Nevertheless, since November 2024, this threat actor has been publicizing leak data from dozens of MOVEit victims, including numerous American energy utilities and service providers.
In the screenshots below, the reader can see various of leaks of personally identifying information (PII) that are linked to either energy utility customers or employees or both. Some of these victims include Texas-based utilities CenterPoint Energy and Entergy, along with Nevada Energy, and Appalachian Power.
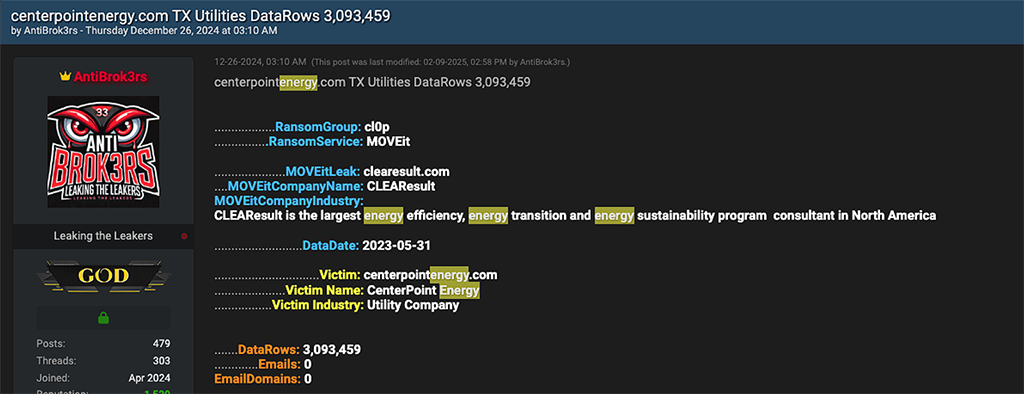
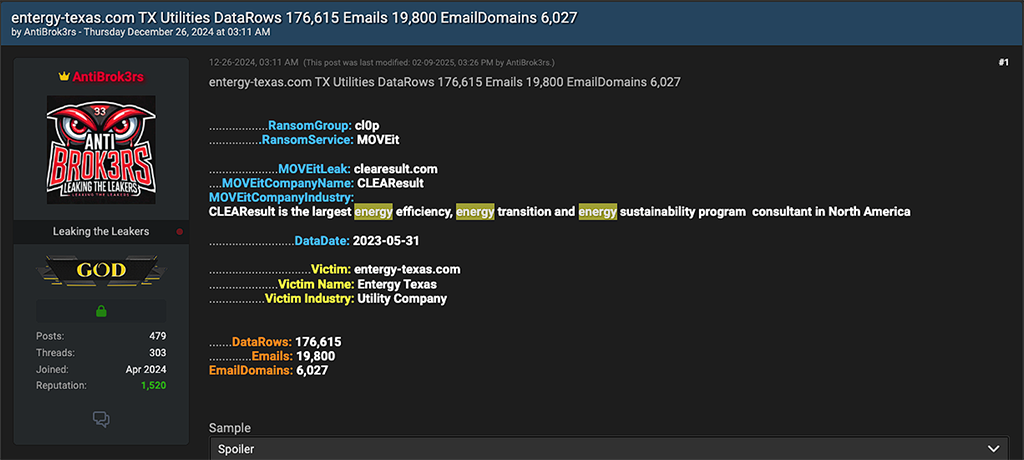
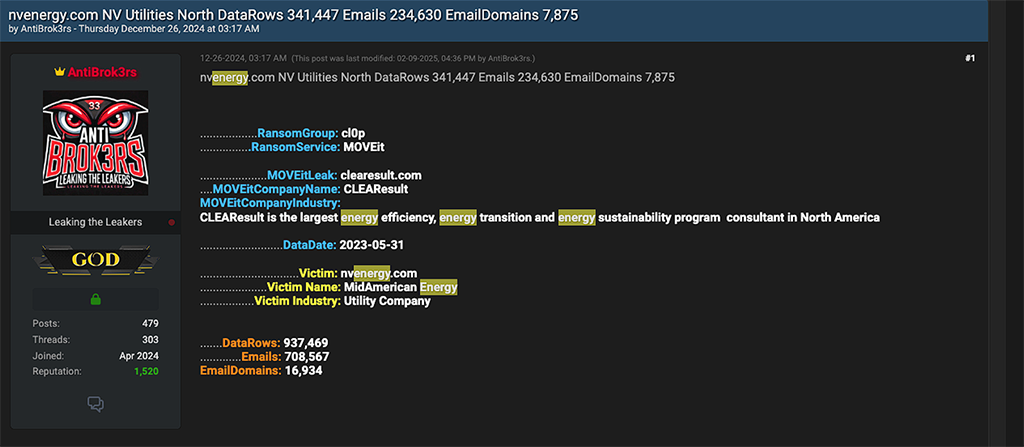
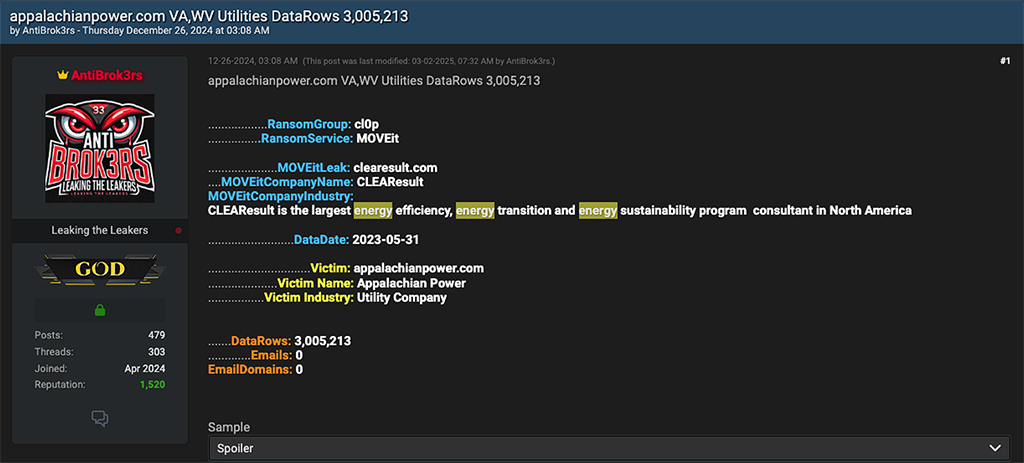
Notably, data from these utilities was compromised from a single MOVEit victim, CLEAResult. CLEAResult is the “largest energy efficiency, energy transition and energy sustainability program consultant in North America,” according to their website. Utility victims shamed by AntiBrok3rs appear to have partnered with CLEAResult to “design and implement their programs,” as indicated by the consultant’s website.
The compromise of these utility companies, which are fourth-party victims to the primary MOVEit managed file transfer breach, highlight the magnitude of cyber supply-chain risk that energy operators must manage today. By breaching MOVEit, Cl0P was not only able to compromise the MFT platforms’ customers, but third parties of those customers as well (fourth parties), exposing a downstream cascade of impacted vendors and clients.
Highlighting the pronounced cyber supply-chain risks facing the energy industry, a joint study published by SecurityScorecard and KPMG in October 2024 found that third-party breaches drive almost half (45%) of malicious intrusions in this sector. According to SecurityScorecard, this figure is “significantly higher than the global rate of 29%. Additionally, 90% of companies that suffered multiple breaches were hit via third-party vendors.”
SecurityScorecard also found that “software and IT vendors outside the energy sector are the main source of third-party breaches.” Of the incidents they reviewed, SecurityScorecard attributed 67% of third-party breaches to software and IT vendors, “with only four involving other energy companies.”
Beyond Cl0P-nexus activity, threat actors connected to the HellCat ransomware group have also been prolific leakers of energy company data. Notably, HellCat claimed responsibility for the November 2024 intrusion of ransomware attack against Schneider Electric, a French multinational energy management firm. Notably, the HellCat ransomware attack marked the third time Schneider Electric had been breached over the preceding 18 months.
HellCat claimed they gained access to the firm via the company Altassian Jira systems. Jira is a project management and issue/bug-tracking tool that is often used by software development teams. According to BleepingComputer, the platform “often contains sensitive data, such as source code, authentication keys, IT plans, customer information, and internal discussions related” to these software development projects.
Notably, HellCat frequently breaches victims by compromising Jira servers. Additionally, a cyber-threat intelligence expert interviewed by BleepingComputer said that HellCat’s signature tactic involves “exploiting Jira credentials harvested from compromised employees that were infected by infostealers.”
In fact, this was the precise staging vector that enabled HellCat to compromise Schneider’s Jira server, according to Hudson Rock research. Specifically, HellCat infected a Schneider Electric employee with Lumma infostealer malware, one of the most prominent infostealer families in the cybercrime ecosystem.
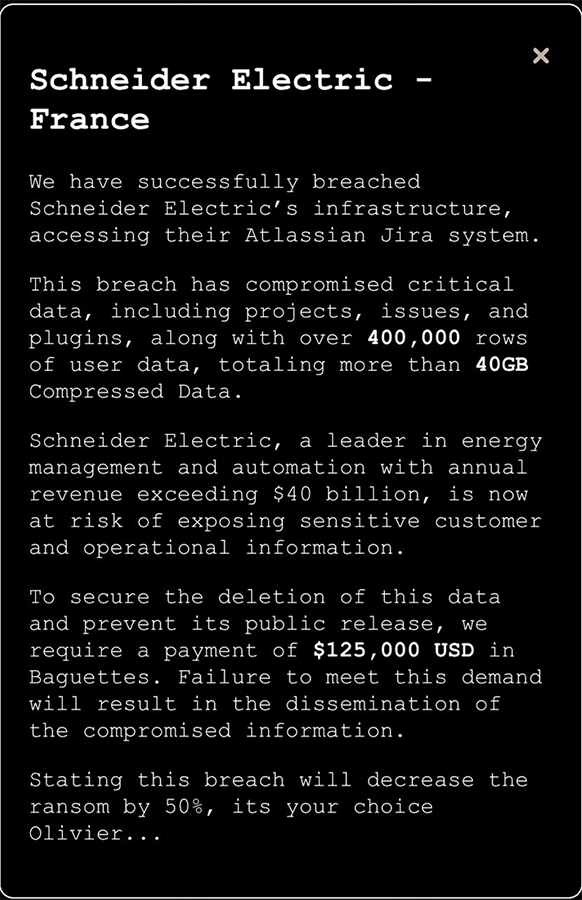
In a ransom announcement that has since been removed from HellCat’s data leak site (DLS), the threat group claimed the “breach has compromised critical data, including projects, issues, and plugins, along with over 400,000 rows of user data, totaling more than 40GB Compressed Data.” In an attempt to be funny, HellCat demanded a “payment of $125,000 USD in Baguettes” to “secure the deletion of this data and prevent its public release.”
It’s not clear if Schneider Electric complied with this specific request, but their ransom announcement is no longer listed on HellCat’s victim-shaming blog. Notably, the nature of this ransom request is distinctly uncharacteristic of those associated with Russia-nexus threat groups, which always demand payment in crypto. This atypically juvenile publicity stunt further guides Resecurity’s medium-confidence assessment that the group’s leadership is unaffiliated with more traditional Russia and CIS-nexus ransomware ecosystems.
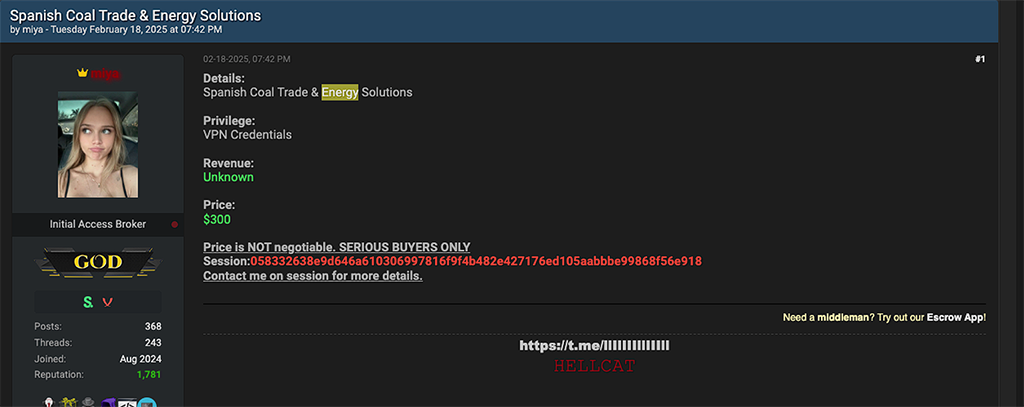
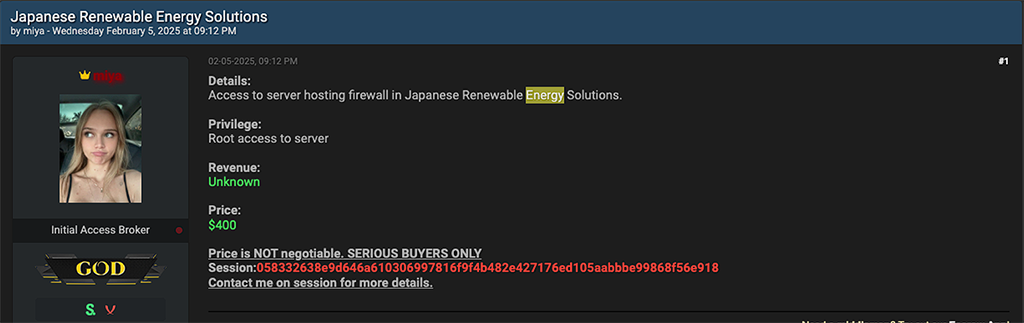
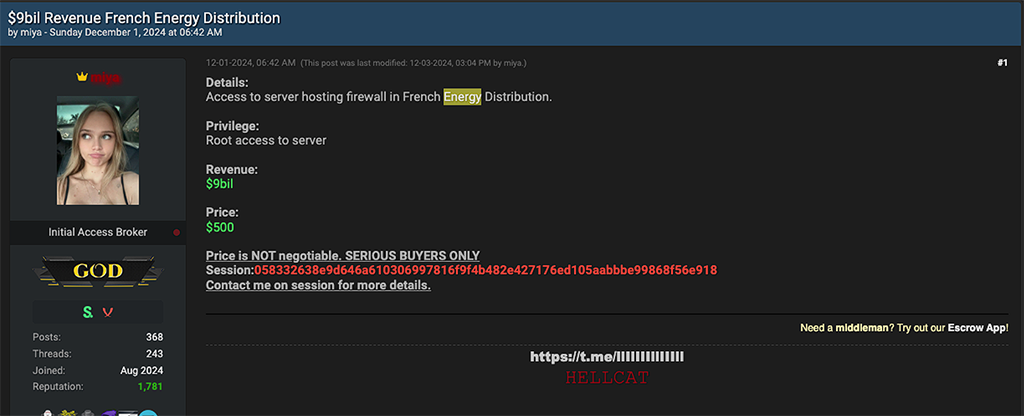
Regardless, HellCat-affiliated threat actors like ‘miya’ have listed access to numerous energy sector victims spanning the globe. Over the last six months miya has published the following access listings on Breach Forums:
- VPN credentials for a “Spanish coal trade and energy solutions” firm
- Root server access for a Japanese renewable energy company
- Root server access for a $9 billion revenue French energy distribution firm
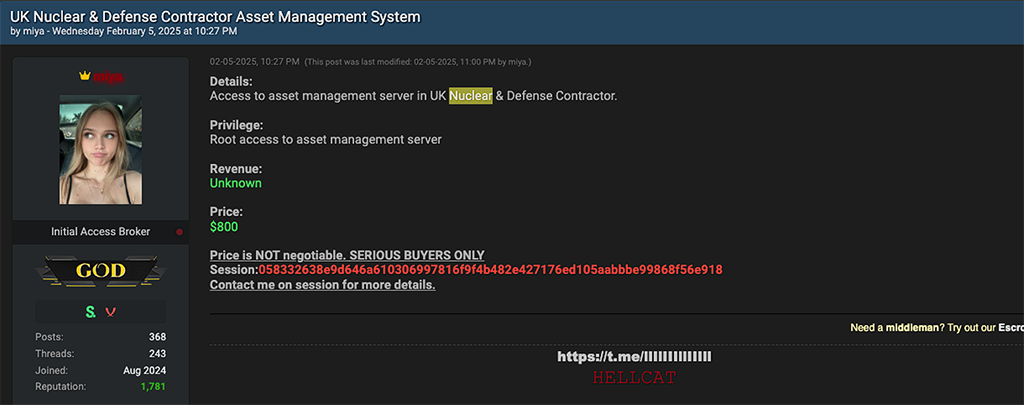
- Root access to an asset management server for a UK nuclear and defense contractor
Listings for these access offerings range from $300 to $800. While the nuclear defense contractor listing is obviously the most alarming, the targeting of renewable energy firms is also noteworthy. Additionally, Resecurity assesses that the nuclear defense contractor access posting is more bluster than an actionable intrusion vector.
Regarding the growing threat to renewable energy, the Federal Bureau of Investigation warned private industry in July 2024 that threat actors are increasingly seeking to “disrupt power generating operations, steal intellectual property, or ransom information critical for normal functionality to advance geopolitical motives or financial gain within the US renewable energy industry.”
The FBI also noted that “structural shifts in the reduced cost of implementation of renewable energy and incentives for development of clean energy have created new targets and opportunities for cyber threat actors to disrupt and exploit for their own gain.” However, the risks highlighted by the FBI are largely applicable to any rapidly growing industry that relies heavily on IIoT-connected devices, according to a UtilityDive report.
Critical infrastructure security experts interviewed by UtilityDive also noted how many renewable energy firms “rely heavily on vendors and third-party organizations for operation and installation.” These enhanced supply-chain dependencies have significantly increased renewable firms’ attack surfaces, making them much easier to breach.
Access & Data Brokers
Other notable energy sector data leaks and access listings observed by Resecurity, and which are at heightened risk of being weaponized by ransomware actors and other threat actors, include:
- 30 GB of confidential data from Qatar Gas, ADNOC Offshore, and Bell Energy
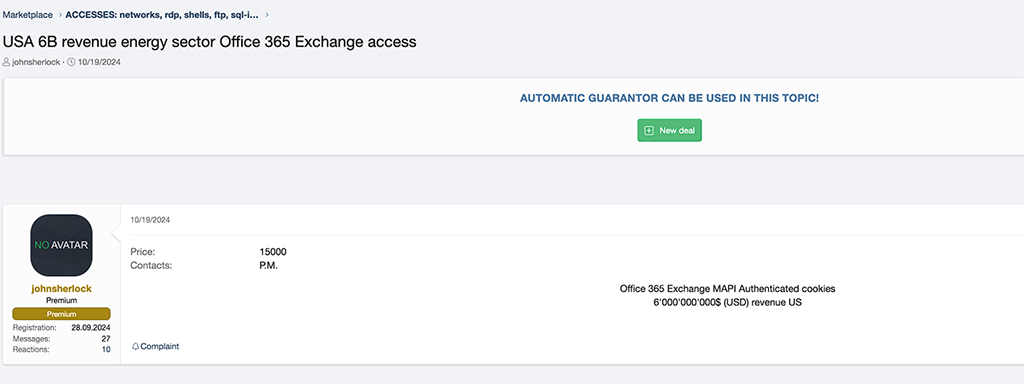
- Office 365 Exchange Access for a U.S. energy firm that generates $6 billion in annual revenue
- Network remote code execution access to “the largest energy company in North Africa”
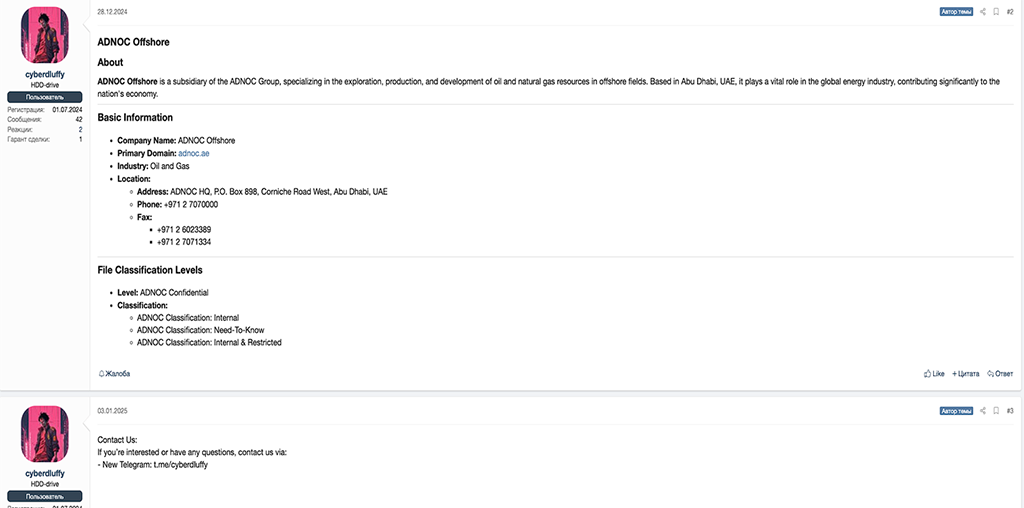
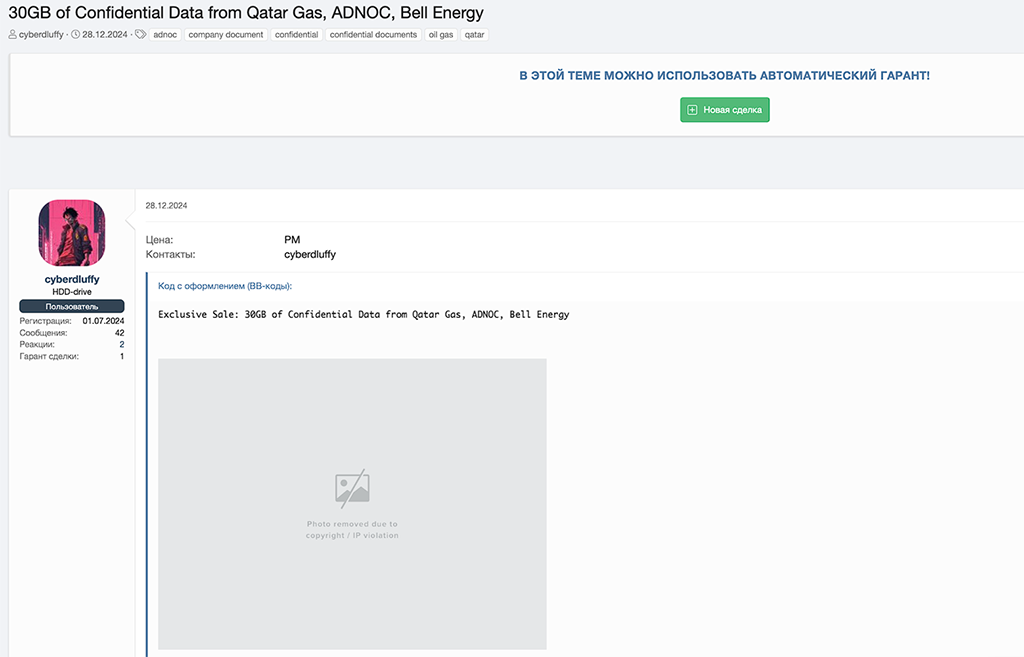
The Emirates-focused data leaks were published on the XSS cybercrime forum on December 28, 2024. QatarGas has recently rebranded as QatarEnergy LNG. The firm is the largest liquefied natural gas company in the world. In the context of the Gaza conflict, the listing of sensitive data connected to this firm is notable and may suggest possible geopolitical motivations.
QatarEnergy is also in the process of developing a $5 billion offshore “megaproject” in a large oil field located in the Persian Gulf, that the Qatari nation jointly owns and shares with Iran.Meanwhile, ANODC Offshore is the largest offshore oil producer in Abu Dhabi. Bell Energy (The Bell Group) is also headquartered in Abu Dhabi. The threat actor who leaked this confidential, Emirates-focused energy data goes by the handle ‘cyberdluffy’ on the XSS forum.
Another noteworthy posting is the Office 365 Exchange access listing for a U.S. energy firm that generates $6 billion in annual revenue. This access listing was posted on the XSS forum on October 16, 2024 by a threat actor who goes by the handle ‘johnsherlock.’ The threat actor listed this access offering for $15,000 USD.
Notably, Microsoft Office 365 has been aggressively targeted by nation-state actors like Midnight Blizzard, AKA NOBELIUM. According to Microsoft threat intelligence analysts, “Midnight Blizzard is a Russia-based threat actor attributed by the US and UK governments as the Foreign Intelligence Service of the Russian Federation, also known as the SVR.” Microsoft also said this “threat actor is known to primarily target governments, diplomatic entities, non-governmental organizations (NGOs) and IT service providers, primarily in the US and Europe.”
Analyzing a malicious campaign that targeted Exchange web services in January 2024, Microsoft noted that threat actors like Midnight Blizzard “compromise user accounts to create, modify, and grant high permissions to OAuth applications that they can misuse to hide malicious activity.” In this campaign, Midnight Blizzard compromised a legacy test 0Auth application to “grant them the Office 365 Exchange Online full_access as_app role, which allows access to mailboxes.”
While there is no substantive link between the johnsherlock access broker persona and Midnight Blizzard, the critical nature of this type of access listing, combined with the geoeconomically sensitive nature of the victim’s industry category (energy), and the relatively high price of the listing, merit closer investigation. If anything, access postings like this illustrate how the line between financially motivated and nation-state cyber-threat activity can often be blurry.
The final noteworthy energy-sector access listing observed by Resecurity is the Breach Forum post that promoted network remote code execution (RCE) access to the “largest energy company in North Africa.” The threat actor who posted this listing is Belsen Group, a nascent, illicit access broker group that gained notoriety in January 2025 for their leak of “configurations from over 15,000 compromised FortiGate firewalls.” Belsen Group has been classified by the cyber threat intelligence (CTI) community as an illicit data broker.
Belsen Group posted their North African energy sector access listing on February 10, 2025, and priced the offering at $20,000 USD.
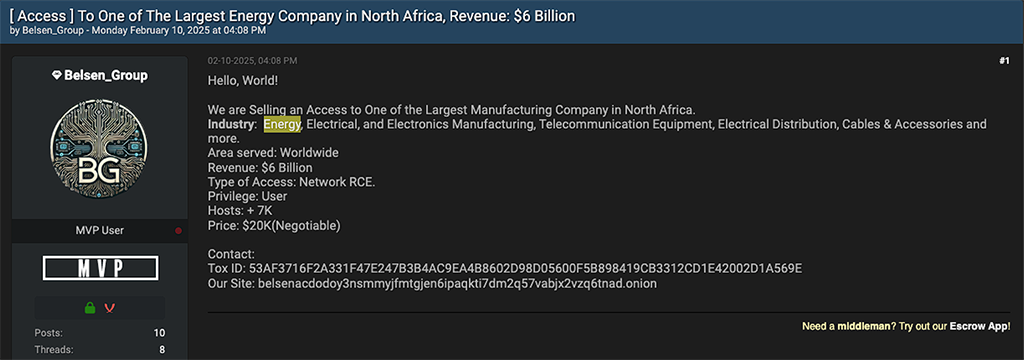
Based on the annual revenue information provided by the threat actor, the alleged victim listed does not appear to be the largest energy company in North Africa. That distinction belongs to Sonatrach, the national state-owned oil company of Algeria, which generates over $77 billion in annual revenue. However, it’s possible Belsen Group misstated the annual revenue for the victim they were claiming.
Hacktivism
Hacktivism is another leading threat targeting the energy sector. Hacktivism is the act of staging cyberattacks in the furtherance of social, political, or ideological change. Most of the geopolitically inspired hacktivist activity documented since the start of the 2022 Ukraine war has manifested as low-level DDoS attacks or web defacements.
But over the last year, HUNTER analysts have observed numerous hacktivist groups claiming successful attacks on energy sector targets in the furtherance of causes aligned with the Russo-Ukraine war and the Gaza conflict. Two prominent pro-Russia hacktivist groups that have generated publicity for their energy-sector targeting, despite general skepticism regarding their claims, are ‘Z-Pentest’ and its partner organization, ‘Sector 16’ (S16).
A December 2024 Cyble report noted that Z-Pentest has “posted videos to their Telegram channels allegedly showing members tampering with operational technology controls (OT), most notably in the oil and gas and water system sectors.”
Cyble noted that those claims “may largely be intended to establish credibility rather than inflict damage on targets.” However, Cyble expressed alarm that, in December, Z-Pentest’s claims “escalated to include disrupting one U.S. oil well system.” Notably, Z-Pentest claims to be based out of Serbia. The group is also aligned with various anti-NATO and pro-Palestine hacktivist groups.
According to the December Cyble report, Z-Pentest claimed to have disrupted “critical systems at an oil well site, including systems responsible for water pumping, petroleum gas flaring, and oil collection.” A 6-minute screen recording posted by the threat actor showed “detailed screenshots of the facility’s control systems, showing tank setpoints, vapor recovery metrics, and operational dashboards allegedly accessed and changed during the breach,” according to Cyble.
In a March 2025 interview with Spanish cybersecurity firm Miólnir, a spokesperson for Z-Pentest pontificated on their hacktivist motivations. This interview was facilitated by another pro-Russia hacktivist group called ‘Noname057(16)’ that we will elaborate on in the following section.
In the Miólnir interview, the Z-Pentest spokesperson referenced the disastrous White House meeting between the Ukrainian and American heads of state, as the commented on the current geopolitical situation:
“We're always on Russia's side, no need to guess. As for Zelensky's circus show in the Oval Office, well, he's better at comedy than military strategy. By the way, we like how Trump mocks the fictional state; at least he has a sense of humor.
As for Europe's leaders… Well, they're a bunch of lost people who don't understand who or what they're dealing with. If they think they're safe, we have to disappoint them: no, they're not. We're everywhere.
Anyone who opposes the Russians is signing a one-way ticket with no return. We don't care who decided to play with fire; we will always defend our own and destroy everything that stands in our way. Want to try your luck? Well, good luck. You'll need it.”
Z-Pentest also denied receiving financial support from state-sponsored actors, telling Miólnir:
“Every time we hear about being sponsored by a government, we laugh so hard we snort coffee. We're not dependent on any country's budget! We have an international crew, and if they made a movie about us, it would be a real box office hit. We're like a big family, where everyone truly lives in harmony (well, except for those who always eat the last slice of pizza).
But if someone decides to support us, say, with a cup of coffee or something stronger—we won't say no!”
However, since the start of 2025, S16 has been the most prolific Russia-nexus hacktivist group targeting the energy sector. Like Z-Pentest, S16 also claims to be based out of Serbia. Including a joint S16-Z-Pentest attack on the Supervisory Control and Data Acquisition (SCADA) system managing oil pumps and storage tanks in Texas, announced in January, S16 has claimed responsibility for five energy-sector attacks around the world.
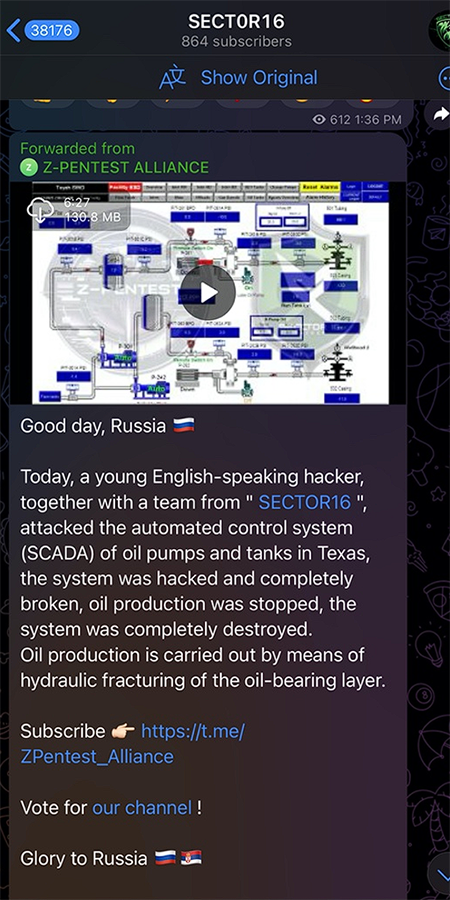
In the Texas SCADA attack, S16 claimed the “system was hacked and completely broken, oil production was stopped, the system was completely destroyed.” However, these claims remain unverified and should be treated with skepticism. Hacktivist groups frequently exaggerate the impact of their breaches to generate hype and spread disinformation. The now-defunct, Russia-nexus DDoS group KillNet is a prime example of this modus operandi.
Beyond the U.S., the group has targeted energy firms in France and Germany. The group’s most recent energy-sector attack claims centered on German “process cooling and refrigeration” firm GEA. The company’s website notes that “GEA’s process refrigeration and gas compression technologies have demonstrated reliable performance in oil & gas, chemical, petrochemical,” and other applications.
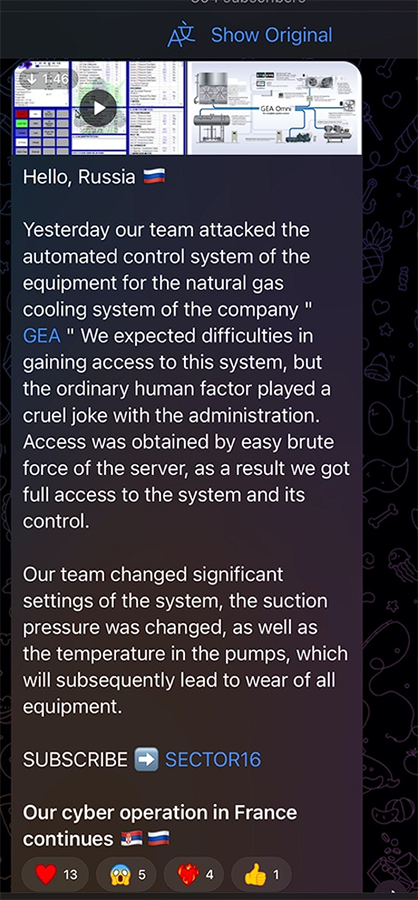
On February 9, S16 announced on their official Telegram channel that they had “attacked the automated control system of the equipment for the natural gas cooling system of the company GEA ." S16 also claimed the attack was enabled by human error, as “access was obtained by easy brute force of the server,” which allowed the hacktivists gain “full access to the system and its control.”
S16 has also been observed partnering with Russia-based hacktivist group OverFlame to target energy facilities. In January, S16 announced they collaborated with OverFlame to attack the “hydroelectric power plants of France, the company "DYNELEC" in the city of Maser-sur-Salat!”
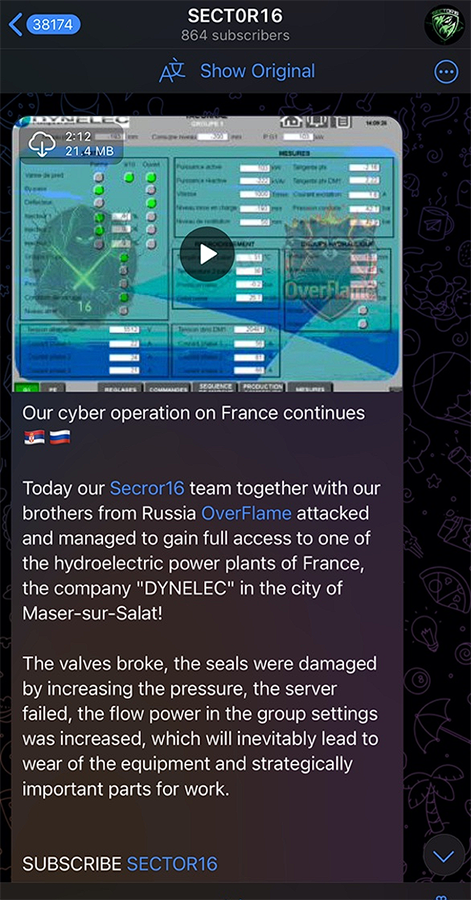
The threat actors claimed the attack inflicted the following cyber-physical damage: “The valves were broken, the seals were damaged by increasing the pressure, the server failed, the flow power in the group settings was increased, which will inevitably lead to wear of the equipment and strategically important parts for work.” Again, these claims remain unverified.
On the Gaza front, leading anti-Israel hacktivist groups engaged in this conflict include ‘CyberAv3ngers’ and ‘Handala.’ Both threat actor groups have been observed targeting the energy sector. A Cybersecurity & Infrastructure Security Agency announcement that was last revised in December 2014 advisory described CyberAv3ngers as a persona used by threat actors affiliated with the Iranian Government’s Islamic Revolutionary Guard Corps (IRGC).
The CISA advisory noted how CyberAv3ngers’ malicious campaigns began in November 2023, just one month after the October 7 massacre. Around this time, these IRGC-affiliated threat actors “began actively targeting and compromising Israeli-made Unitronics Vision Series programmable logic controllers (PLCs) and human machine interfaces (HMIs),” according to CISA.
CISA also noted that CyberAv3ngers left defacement images on victim websites stating, “You have been hacked, down with Israel. Every equipment ‘made in Israel’ is CyberAv3ngers legal target.” PLCs targeted in this attack campaign are “commonly used in the Water and Wastewater Systems (WWS) Sector and used in other industries including, but not limited to, energy, food and beverage manufacturing, transportation systems, and healthcare,” according to CISA.
Again, CyberAv3ngers’ targeting activities highlight the unique supply-chain threat that energy sector firms face, particularly in the context of external geopolitical conflicts. In this IRGC-nexus campaign, for example, all critical digital assets (CDAs) manufactured by Israel have been deemed legitimate military targets, thus threatening enterprise customers of these products with potentially catastrophic collateral damage.
Handala is another prolific Gaza-nexus threat actor that has attracted the attention of the CTI community for their bold claims of energy sector hack-and-leak operations and similar campaigns in other sectors. Regionally, Handala’s targeting has been focused on Israeli entities.
In a July 2024 CTI report documenting a Handala wiper malware campaign that opportunistically exploited the widespread CrowdStrike Falcon outage, Trellix said the group “at least pretends to act based on pro-Palestinian motives,” but cautioned this posturing could be a “façade for an ulterior motive.” This assessment is common for most high-level hacktivist activity, which can easily serve as cover for nation-state espionage or disinformation operations.
Energy sector victims allegedly compromised by Handala include:
- BLEnergy – a leading battery energy storage systems (BESS) integrator and provider in Israel
- ELitech - a company providing engineering and project management services to renewable energy, private power plants, gas insulated substations (GIS), defense and military projects, and projects requiring a high degree of technological expertise
In July 2024, Handala published a post on the RAMP cybercrime forum announcing that the hack and leak of 145 GB of data belonging to BLenergy. This attack again highlights the growing threat to companies that operate in the renewable energy space.
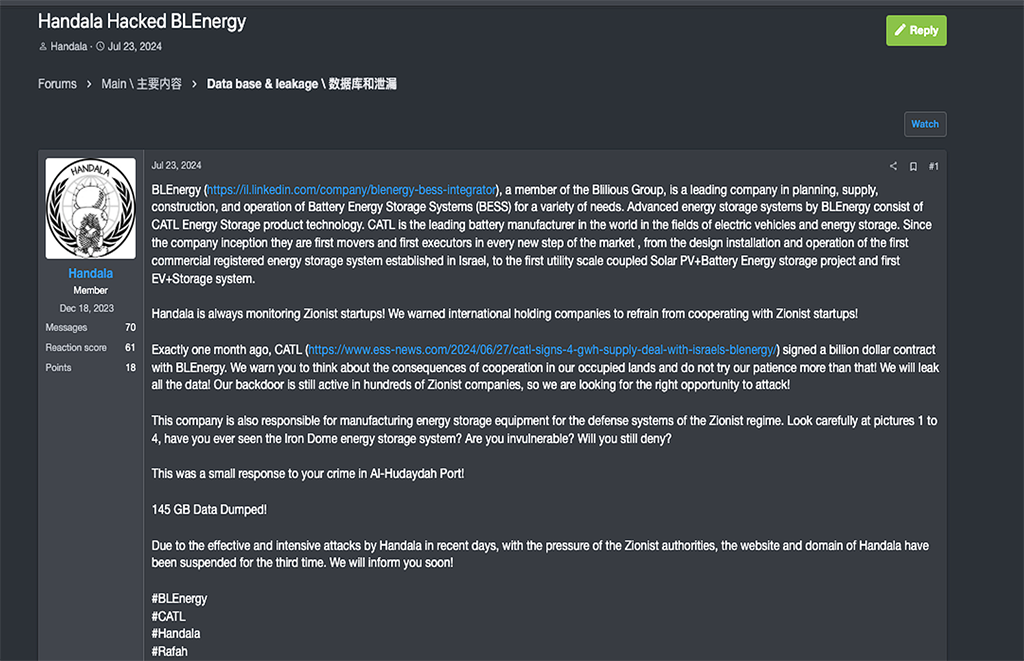
Highlighting related supply-chain risks and targeting, Handala’s post noted that exactly one month prior to their claimed attack, “CATL signed a billion dollar contract with BLEnergy.” “CATL is the leading battery manufacturer in the world in the fields of electric vehicles and energy storage,” according to Handala’s post.
Handala also warned the victim to “think about the consequences of cooperation in our occupied lands and do not try our patience more than that! We will leak all the data! Our backdoor is still active in hundreds of Zionist companies, so we are looking for the right opportunity to attack!”
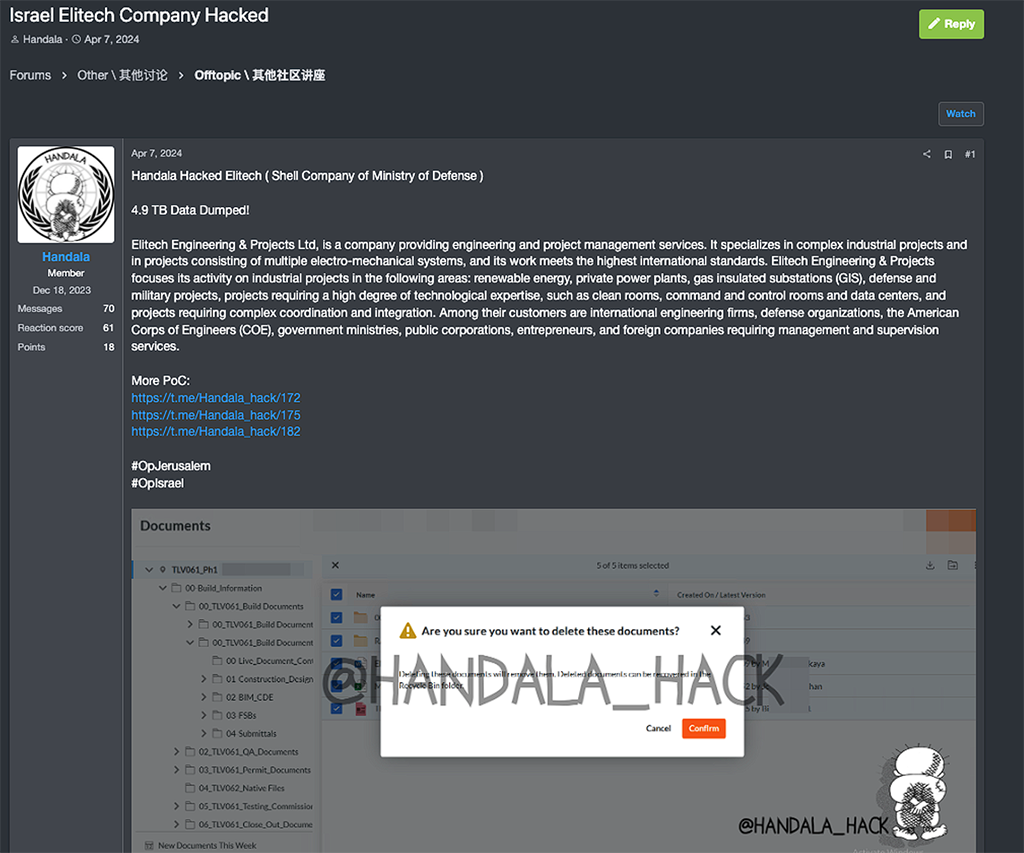
In April 2024, the threat actor also announced on the RAMP forum that they had hacked and leaked 4.9 terabytes of data belonging to Elitech. Notably, this attack included the hashtags #OpIsrael and #OpJerusalem. Resecurity has previously chronicled #OpIsrael-related hacktivist campaigns that ensued in the wake of the October 7 massacre.
Nuclear Access and Data Leaks
Alarmingly, threat actors have also escalated their targeting of the nuclear sector. These attacks have ranged from intricate job recruitment and phishing schemes targeting nuclear sector personnel to allegations of stolen data, access listings, and claims of successful DDoS attacks.
Over the last year, the most notorious adversary confirmed to have attacked nuclear sector targets is Lazarus Group, a North Korean state-backed advanced persistent threat (APT) group that has gained infamy for its high-ticket crypto hacks. In December 2024, Kaspersky documented their findings from a Lazarus campaign they dubbed “Operation DreamJob.”
An investigation conducted by Kaspersky revealed that several employees from a nuclear-related organization were “infected via three compromised archive files appearing to be skill assessment tests for IT professionals.” This ongoing campaign “leverages a range of advanced malware, including a newly discovered modular backdoor, CookiePlus, that was disguised as open-source plugin,” according to Kaspersky.
Combing the dark web, HUNTER analysts discovered a variety of alleged nuclear-related access listings, data leaks, and claims of successful DDoS attacks. HUNTER findings include:
- Malaysian Nuclear Agency database leak
- Emirates Nuclear Energy Corporation data leak
- VPN access for a Greek nuclear energy company
- Electric Power Research Institute (EPRI) database
- GE network logins, including access to nuclear power plants
- DDoS attack on Framatome in France
- DDoS attacks on Doel and Tihange nuclear plants in Belgium
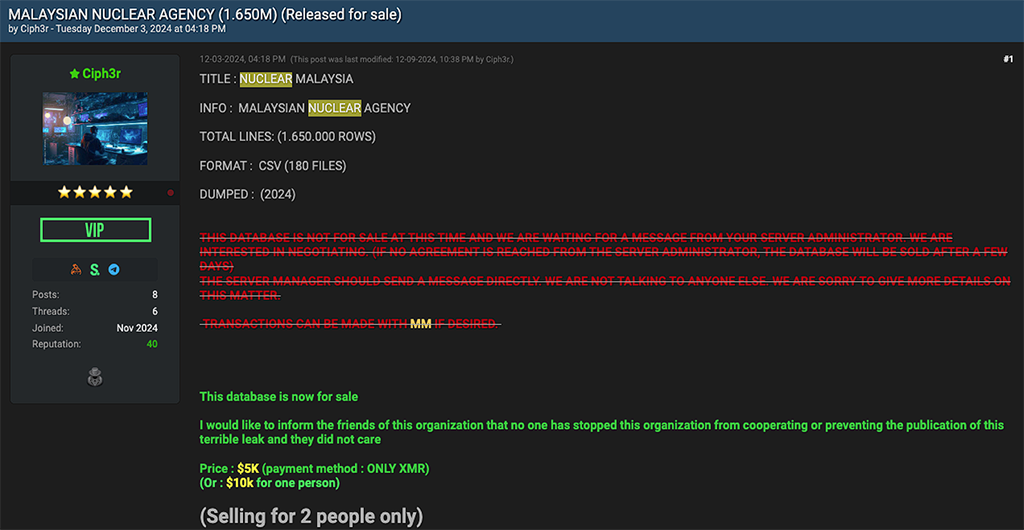
The Malaysian Nuclear Agency database leak was posted on Breach Forums on December 3, 2024 by a threat actor who goes by the handle ‘Ciph3r.’ This victim is a nuclear technology research facility. The threat actor listed non-exclusive access to the data for $5,000 USD. Meanwhile, Ciph3r priced exclusive access to the data (meaning the database would be sold to only one buyer) at $10,000 USD.
This access listing comes at a time when Malaysia is actively exploring a strong pivot into nuclear energy to facilitate their transition away from coal-powered plants. Another noteworthy data leak is the ENEC listing posted by threat actor ‘WalkerATX’ on Breach Forum in January 2025.
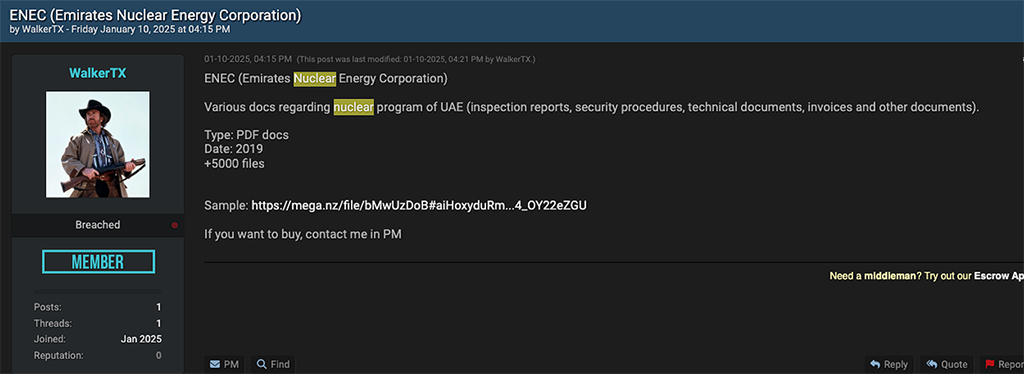
In this post, the threat actor claims to have access to over 5,000 stolen PDF files related to the United Arab Emirates nuclear program, including inspection reports, security procedures, technical documents, invoices, and other documents. WalkerTX also said these files are as current as 2019. The threat actor did not list a price for this data.
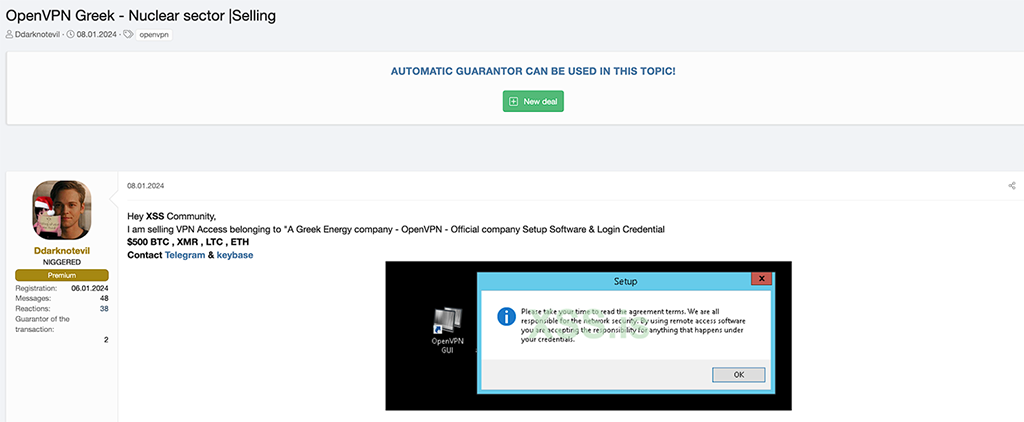
In addition to the ENEC posting, HUNTER analysts found an OpenVPN access listing for a Greek nuclear energy firm on the XSS forum. A threat actor who goes by the handle ‘Ddarknotevil’ posted this listing in January 2024 and priced the access offering at $500 in crypto.
HUNTER analysts also found a Breach Forums listings from July 2024 where threat actor ‘bdbdbhdctvhdvf’ claimed that he was selling access to “all EPRI data,” including 100,000 customers.
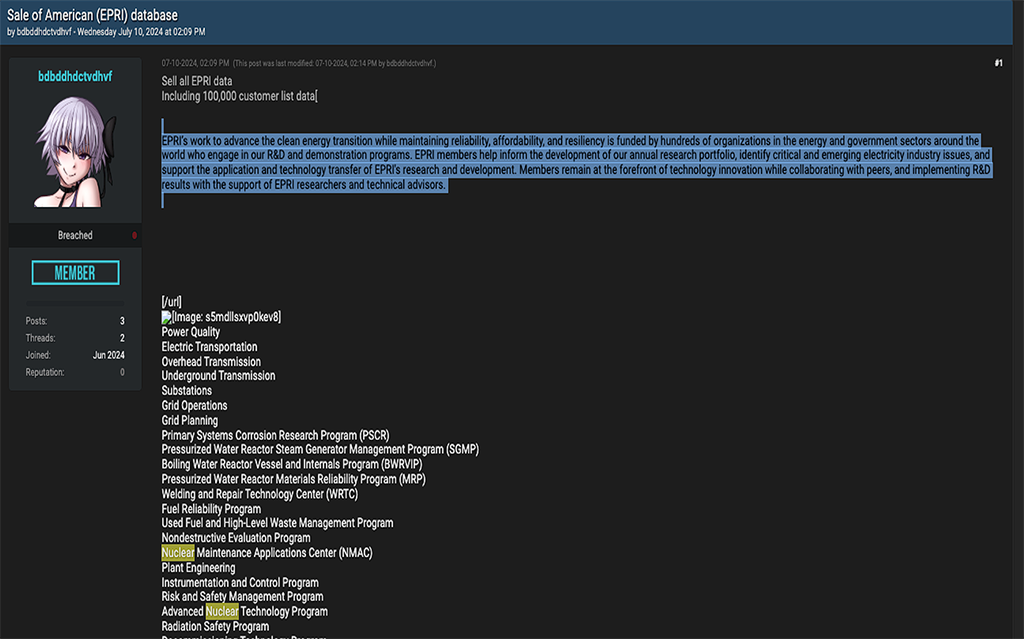
According to EPRI’s Wikipedia page, the institute is an American “independent, nonprofit organization that conducts research and development related to the generation, delivery, and use of electricity to help address challenges in the energy industry, including reliability, efficiency, affordability, health, safety, and the environment.” Notably, EPRI has a significant nuclear research focus, as indicated by their website. The Breach Forums post also highlights EPRI’s expertise in nuclear maintenance applications and advanced nuclear technology programs.
Another nuclear-related access listing discovered by HUNTER analysts is related to a January 2025 XSS post authored by threat actor ‘l4u6h1n6m4n.’ The threat actor claimed to have administrative credentials and network access for multinational energy firm General Electric (GE). This access listing claimed to include administrative passwords for routers, switches, F5s, WASS’s, ISE, firewalls, and proxies. The threat actor also said the access package featured network diagrams, supporting documentation, and “export control parts of the network.”
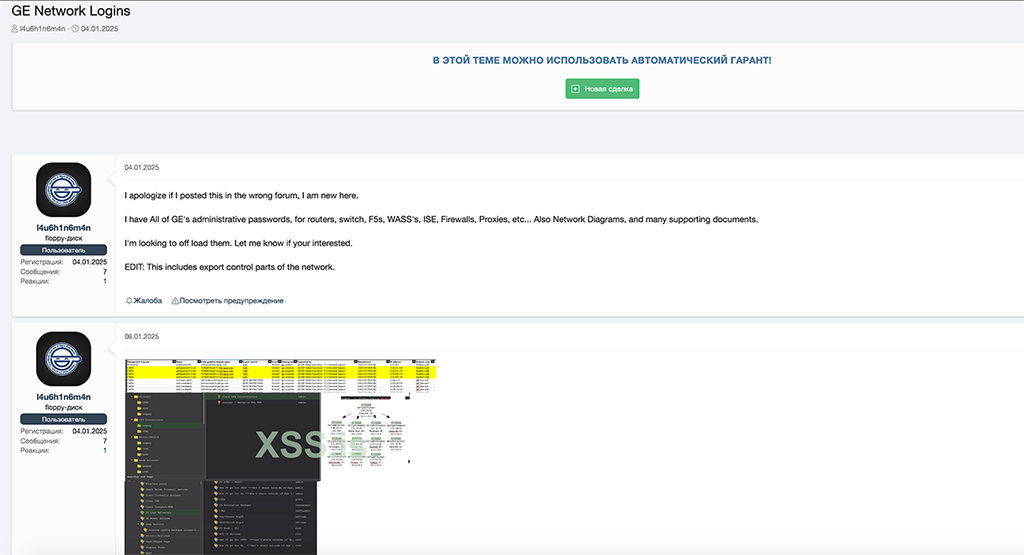
By citing the export control part of GE’s network, the threat actor is likely referencing servers or databases storing classified or controlled technical data, network segments linked to military contracts, or sensitive R&D.
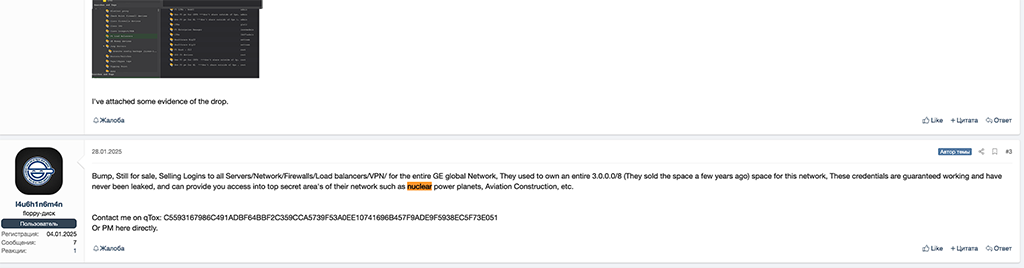
On January 28, the threat actor wrote a follow-up post to their initial thread and claimed the GE global network access credentials offer entry points to servers, network devices, firewalls, load balancers, and VPN accounts. The threat actor also said these logs enable access to “top secret area's” of GE’s network, including nuclear power plants.
Lastly, HUNTER analysts uncovered three DDoS announcements that referred to alleged attacks on nuclear sector targets in France and Belgium. These attacks were conducted by Z-Pentest collaborators Noname057(16). Notably like S16, Noname057(16) is a pro-Russian hacktivist group that also prominently features the number 16 in their naming convention.
Additionally, in the Miólnir interview the Z-Pentest spokesperson makes it a point to highlight the significance of this number, as they provided the following editorial correction to their interviewer:
“We'd like to correct a small error: instead of NoName057, it should be NoName057(16). It's just numbers, but it's very important.”
It is unclear if there is a substantive working connection between S16 and Noname057(16). Nevertheless, both groups cooperate with Z-Pentest and both emphasize the number 16 for reasons that likely share symbolic significance. Noname057(16) has previously been observed targeting victims in the UK, Ukraine, South Korea, the Czech Republic, and Japan.
On March 13, Noname057(16) claimed to have executed a successful DDoS attack on Framatome, a rench nuclear reactor company jointly owned by public utility Électricité de France and Mitsubishi Heavy Industries.
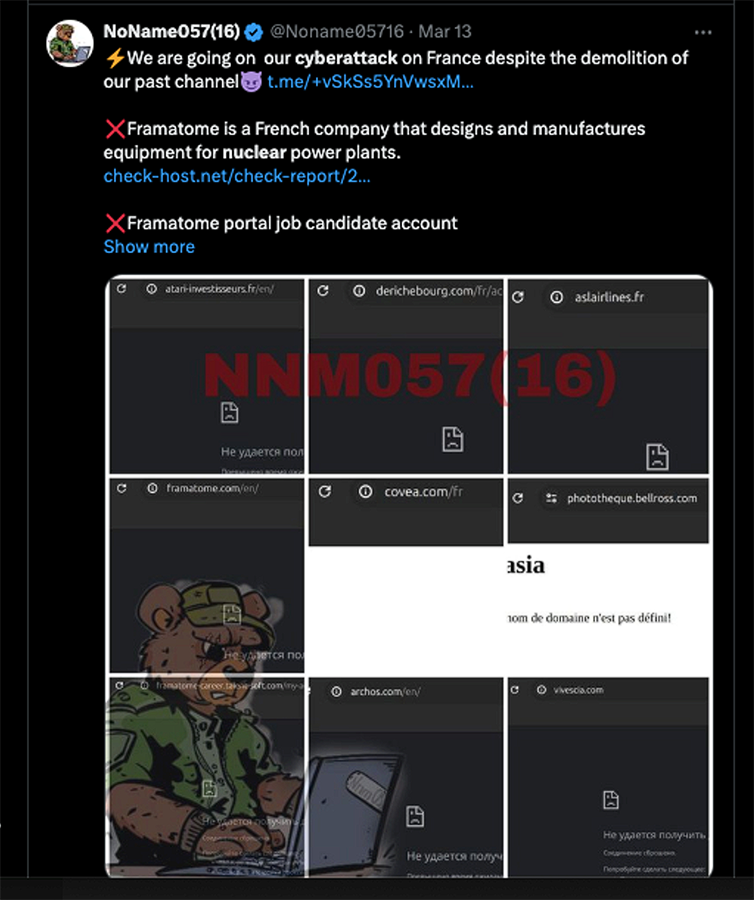
Framatome “designs, manufactures, and installs components, fuel and instrumentation and control systems for nuclear power plants and offers a full range of reactor services,” according to the company’s Wikipedia page.
Noname057(16) claimed to have conducted two more nuclear sector DDoS attacks on April 1, 2025. These attacks allegedly impacted the public-facing websites targets in Belgium: Doel and Tihange. The facilities represent half of Belgium’s four nuclear reactors, according to the World Nuclear Association.
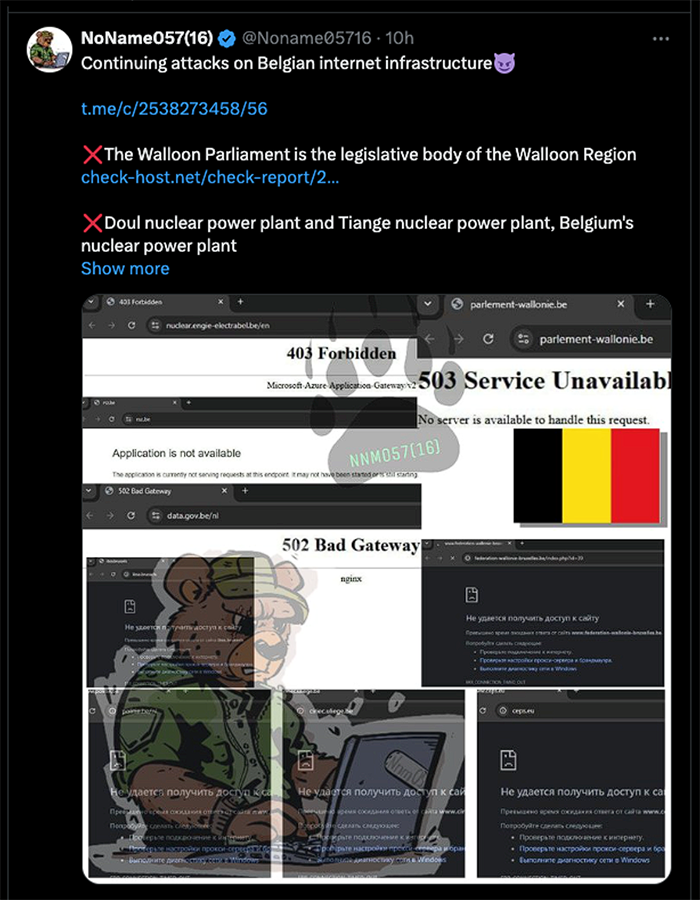
It is unclear how effective or impactful Noname057(16)’s DDoS attacks on these three nuclear targets were. However, it should be noted that there was no risk to the proper functioning of OT and related critical digital assets (CDAs) in the nuclear facilities publicly shamed by the threat actor.
The primary reason it is extremely difficult to compromise or otherwise disrupt nuclear power operations through cyber-enabled means is that these energy facilities mandate the implementation of air-gapped networks by default. This means that industrial control systems (ICS), SCADA infrastructure, and other CDAs are physically isolated from the external networks, including the public Internet.
Additionally, these facilities enforce extremely strict network segmentation between business IT and physical OT networks. In theory, this framework makes lateral movement from a compromised IT system into an OT environment impossible. Furthermore, the data flow in nuclear energy facilities is designed to be unidirectional by default. This mean that data can only flow out of the plant environment, while no data is allowed to enter the facility’s network.
According to Mark Rorabaugh, the President of InfraShield, a critical infrastructure security firm with unique expertise in protecting nuclear power facilities, the primary risk to these entities emerges from physical sabotage conducted by malicious insiders. “The specific attack vector that nuclear energy operators must be on high alert for is malicious portable media introduced into the plant environment by a rogue employee or contractor,” according to Rorabaugh.
Nevertheless, while Noname057(16)’s attacks are relatively unsophisticated, HackManac highlighted them as the most active threat group for the week dated March 19-25 2025. The threat group accounted for 135 of 574 confirmed cyberattacks that week, illustrating their significant level of threat activity. The group’s second-degree (and perhaps more expansive links) to S16 is also a nexus nuclear-sector defenders should monitor closely, given the latter’s alarming and increasing claims of successfully compromising OT and SCADA systems.
Significance
Resecurity’s second energy-sector CTI report documents the HUNTER unit’s latest findings of malicious activity targeting these critical infrastructure organizations. In a geopolitical backdrop fractured by ongoing conflicts in Ukraine and Gaza, HUNTER’s findings largely demonstrate how military hostility is projected into cyberspace and how ancillary cybercriminal ecosystems support the malicious targeting of energy firms.
For energy-sector defenders, the findings of this report should serve as a warning that threat actors are escalating their attacks on these critical infrastructure organizations and growing increasingly bolder when it comes to targeting their OT networks. In this threat landscape, the potential for a catastrophic cyber-physical attack that causes environmental or human harm is rapidly increasing.
The most prominent threat actors recently identified by HUNTER as actively targeting the energy sector include the following:
- RansomHub/DragonForce [Ransomware]
- HellCat [Ransomware]
- Lazarus Group [Nation-State]
- Cyb3rAv3ngers [Nation-State]
- S16 [Hacktivist]
- Noname057(16) [Hacktivist]
Based on this compilation of leading threat actors, defenders should be especially aware of HellCat’s tactics, techniques, and procedures (TTPs), specifically their reliance on infostealer attack chains, with an emphasis on Lumma malware. Given this targeting activity, defenders should regularly conduct comprehensive dark web monitoring to audit their personnels’ and IT/software supply-chain partners’ exposure to credential compromise. The latter is particularly vital as SecurityScorecard and KMPG research revealed that the IT and software supply chain is the energy sector’s weakest link.
Conclusion
In response to these growing threats, the U.S. Department of Energy (DOE) issued new cybersecurity guidelines for electric distribution systems and distributed energy resources (DER) in 2024. These guidelines, developed in collaboration with the National Association of Regulatory Utility Commissioners (NARUC), aim to provide a common framework for reducing risk and improving the cyber resilience of critical infrastructure.
Resecurity warns about the increase in targeted cyberattacks against enterprises in the energy sector worldwide. Some of these attacks represent much larger campaigns designed to target country-level infrastructure, acting as tools for geopolitical influence. It is expected that nation-state actors and foreign intelligence will leverage this approach as a new generation of warfare in the future, where the role of cybercriminal actors may be significant, enabling further cyberattacks and providing infrastructure and resources to conduct offensive cyber operations.

