
Introduction
NFC-related fraud is on the rise, as evidenced by cyber threat intelligence analysts at Resecurity. Numerous banks, FinTechs, and credit unions have reported increased NFC-related fraud and highlighted significant challenges in early detection. Chinese cybercriminals demonstrate high adaptability in exploiting NFC technologies for fraudulent purposes and create new tools to facilitate illegal operations at scale. They target financial institutions to defraud consumers and cause substantial economic losses for the global economy.
Cybercriminals leverage NFC fraud against ATMs and POS terminals, stealing money from consumers at scale. Resecurity investigated multiple incidents identified in Q1 2025, exceeding several million dollars in damages for one of the top Fortune 100 financial institutions in the United States due to NFC fraud. Stopping cybercriminals operating from China presents significant challenges due to geopolitical, technical, and organizational factors.
Many cybercriminal activities in China are believed to be part of larger organized crime syndicates that are state-sponsored, state-encouraged, or state-tolerated. The Chinese government and the Chinese Communist Party (CCP) have been accused of supporting cyber operations that target foreign governments, businesses, and individuals. Additionally, China has accused other nations, such as the United States, of engaging in cyberattacks, further complicating the issue.
Such groups' operations extend beyond Chinese borders, and these actors effectively utilize international networks for fraudulent activities. Resecurity outlines that the regions most affected include the U.S., the UK, the EU, Australia, Canada, New Zealand, Japan, South Korea, the Philippines, the UAE, and Saudi Arabia.
From NFCgate to Track2NFC - The Origin of Contactless Fraud
Considering the relatively new technology, the first incident involving NFC fraud (or "carding") is not explicitly documented. However, the technology behind NFC (Near Field Communication) has been around since the early 2000s, with the first NFC-enabled phone launched by Nokia in 2006. While specific incidents of NFC carding may not have a clear date of origin, the rise of contactless payment systems and cybercriminals' subsequent exploitation of these technologies began to gain attention in the late 2000s and early 2010s. As NFC technology became more widespread, reports of fraud and carding incidents started to emerge, mainly as mobile payment systems like Google Wallet and Apple Pay were introduced.
Such wallets leverage NFC technology to facilitate secure and convenient contactless payments, enabling consumers to make payments by simply tapping their NFC-enabled smartphones against compatible payment terminals. When a user initiates a payment, a wallet generates a unique encrypted payment code transmitted to the NFC-compatible terminal. This code masks the user's card number, enhancing transaction security. NFC has transformed how consumers engage in transactions, providing a fast, secure, and user-friendly payment solution. By enabling contactless payments and integrating additional features, payment providers have enhanced the overall shopping experience for consumers, which is why this technology is rapidly developing. Today, it is estimated that 1.9 billion phones worldwide are NFC-enabled, showcasing its rapid adoption.
The fact that credit card (CC) information is already stored on the device and added to the wallet immediately triggered the attention of cybercriminals. They started to design new techniques and tools to leverage NFC and mobile wallets to perform illegal transactions and steal money from victims.
In 2020, students at the Technical University of Darmstadt, Germany, developed NFCgate to capture, analyze, or alter NFC traffic. Their research has immediately attracted the attention of cybercriminals who created the malware called NGate, leveraging principles they described - the malicious tool relayed NFC data from victims’ payment cards, via victims’ mobile phones, to the device of a perpetrator waiting at an ATM. Cybercriminals didn't limit themselves to ATMs. The "Ghost Tap" technique enables cybercriminals to cash out money from stolen credit cards linked to mobile payment services such as Google Pay or Apple Pay by relaying NFC traffic via NFC-enabled POS terminals. In this case, bad actors "tap" their mobile devices with stolen, compromised data to make fraudulent transactions. Therefore, the merchandise can be “purchased” at the POS terminal, but the credit card terminal will not submit the transaction for payment to the merchant’s payment processor.
October 2024 - The Texas Financial Crimes Intelligence Center alongside the U.S. Secret Service (USSS) and the Federal Bureau of Investigation (FBI) released an advisory highlighting issues to counter a merchant processing vulnerability due to an app threat dubbed “Track2NFC.” The app duplicates an NFC transaction and utilizes specific card numbers and NFC tokens to force merchant payment terminals into an offline transaction mode. Around
that time, cybercriminals' first efforts to develop special tools to
enable NFC-based carding were identified. Notes were detected on
multiple forums on the Dark Web that using NFC may be less suspicious
than traditional carding methods.
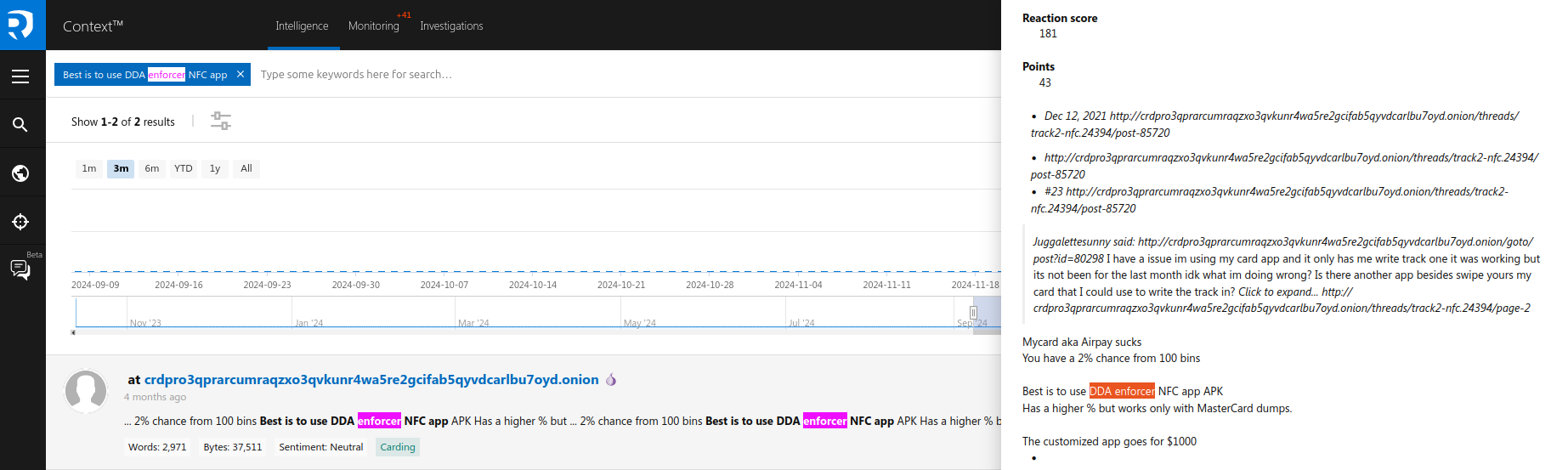
Resecurity observed several postings where cybercriminals discussed the tools to use for NFC fraud. These include legitimate applications that allow users to store, manage, and process NFC-enabled credit cards, such as Mycard and Airpay. Cybercriminals highlighted the option of developing customized NFC apps starting from $1,000 on the Dark Web.
Cybercriminals create "farms" of mobile devices to automate NFC fraud at scale. Our investigators identified Chinese actors operating tens of devices simultaneously via customized server relaying NFC transactions to POS terminals.

Primarily, the actors use Android-based phones, with numerous cards "loaded" into mobile wallets for further fraud. In one such instance, cybercriminals specifically focused on fraud automation against Barclays, Lloyds, Halifax, HSBC, WISE, Santander, Bank of Scotland, and Revolut.
The Anatomy of NFC-based Carding
How do those apps work? They all use Host Card Emulation (HCE) to mimic a physical ISO 14443 NFC smart card by registering a service that extends HostApduService. This allows the app to respond to APDU command sequences like a card.
APDU (Application Protocol Data Unit) commands are the standardized communication units used between a smart card reader and a smart card. They are essential for executing operations on smart cards, such as reading data, writing data, or performing cryptographic functions.
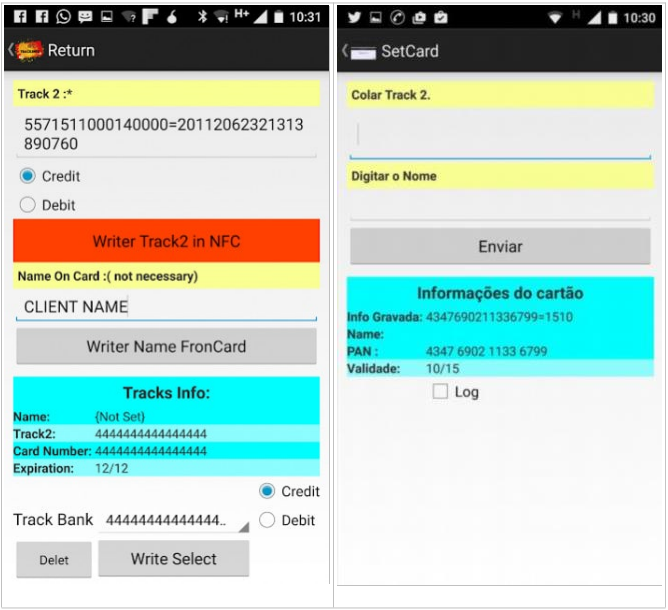
For example, Track2NFC allows you to convert magnetic stripe data (Track 2). You can use the app to store the information on your mobile device and make purchases at any NFC-enabled terminal. Such an app can be used for legitimate purposes, such as when developers of payment services test NFC-compatible apps, but obviously, cybercriminals use it for malicious purposes. The app can support multiple credit or debit cards. This means you can store information for all your cards in one convenient location, making it easy to switch between cards when purchasing.
Independent developers have designed multiple applications supporting HCE. One of them, "HCE Bridge", simulates and implements all six EMV Contactless Kernels, including PayPass, PayWave, Expresspay, J/Speedy, D-PAS, and QuickPass. The app is available for 100$ and was created for educational purposes. This application, developed by iso8583.info, acts as a bridge for testing various card profiles supported by its service, iso8583.info. It emulates the Host-Card-Emulation (HCE) process, simulating card-terminal interactions and APDU (Application Protocol Data Unit) exchanges. Cybercriminals exploit the same approach by manipulating HCE for malicious purposes to process compromised credit card data via NFC.
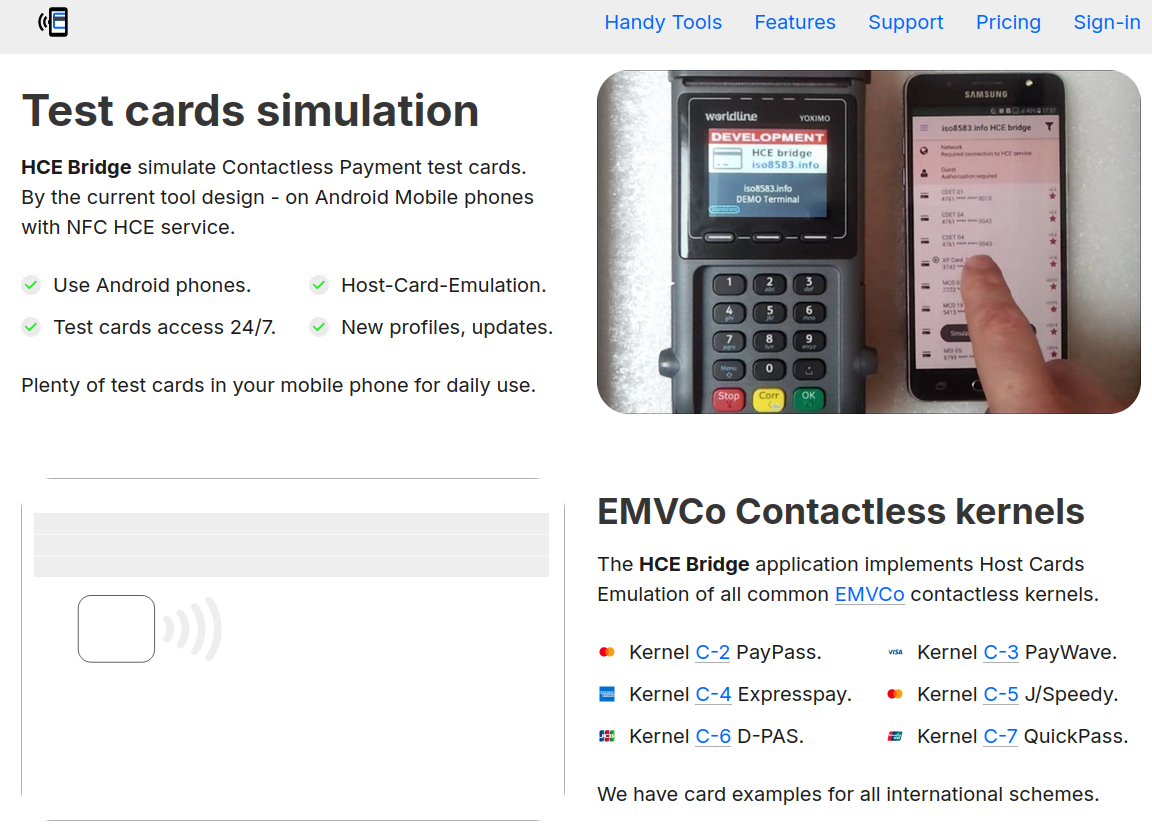
HCE Bridge supports multiple types of cards enabling contactless payments.
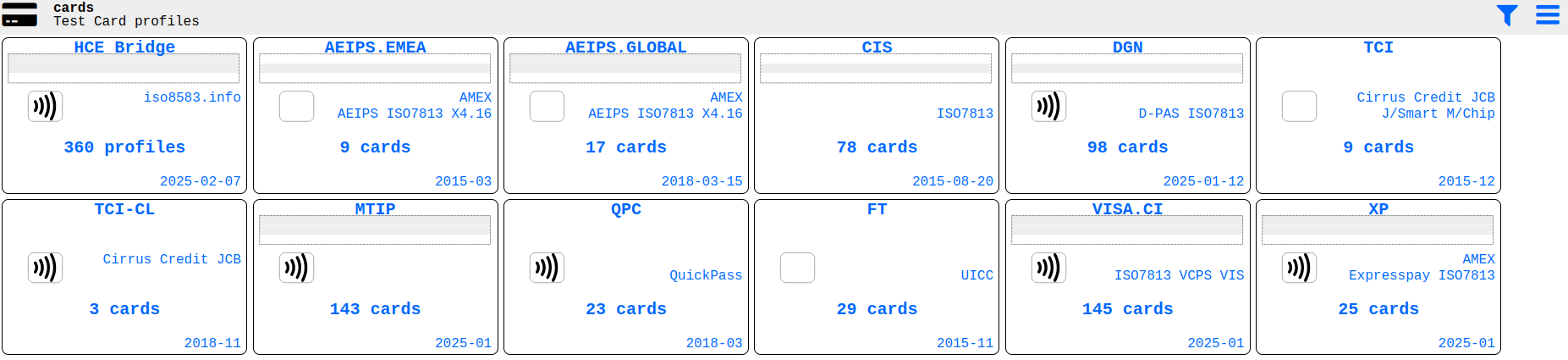
HCE Bridge provides debugging functions and detailed output. Considering its inexpensive licensing the app gives valuable insights into NFC technology and its further implementation into cybercriminal tools.

Notably, some similar tools have restrictions purposely defined by developers, understanding that carders may leverage them for malicious purposes. For example, another app with similar features Credit Card Reader NFC (EMV) 5.1.4 (nodpi) doesn't access the Internet (No Internet permission) and the operator needs to confirm credit card details manually.
Chinese Carding Underground Ecosystem
Resecurity identified multiple Chinese cybercriminal groups targeting Google and Apple Wallet customers. Their modus operandi centers on the abuse of NFC payments and the misuse of technology to conduct fraud. Our analysts from the HUNTER unit identified a group on Telegram offering the Z-NFC tool for sale to facilitate fraudulent transactions. Another tool, called King NFC, was previously marketed on the Dark Web as an alternative. Notably, the Telegram channels offering it are named X-NFC, which may create some confusion. The actors behind the tool provide technical support and guidance on how to use it.
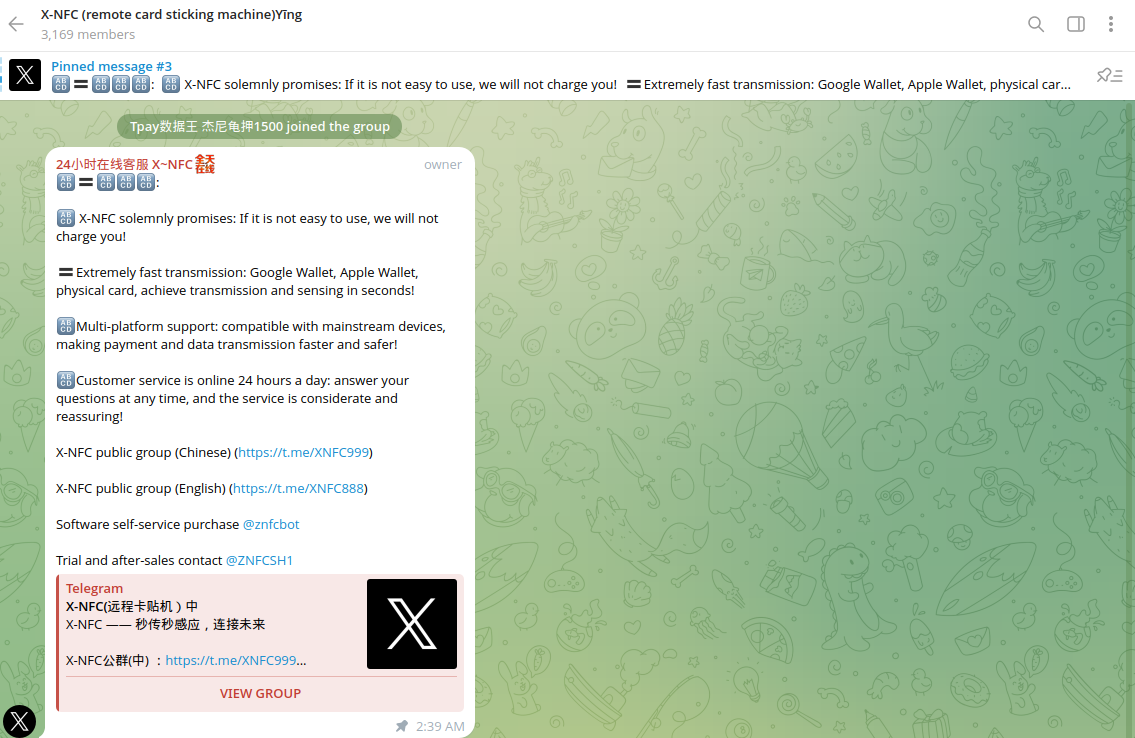
The tool is offered on a subscription basis. After successful payment for license activation, it can be downloaded as an Android software installation package from a host generated by the Telegram bot.
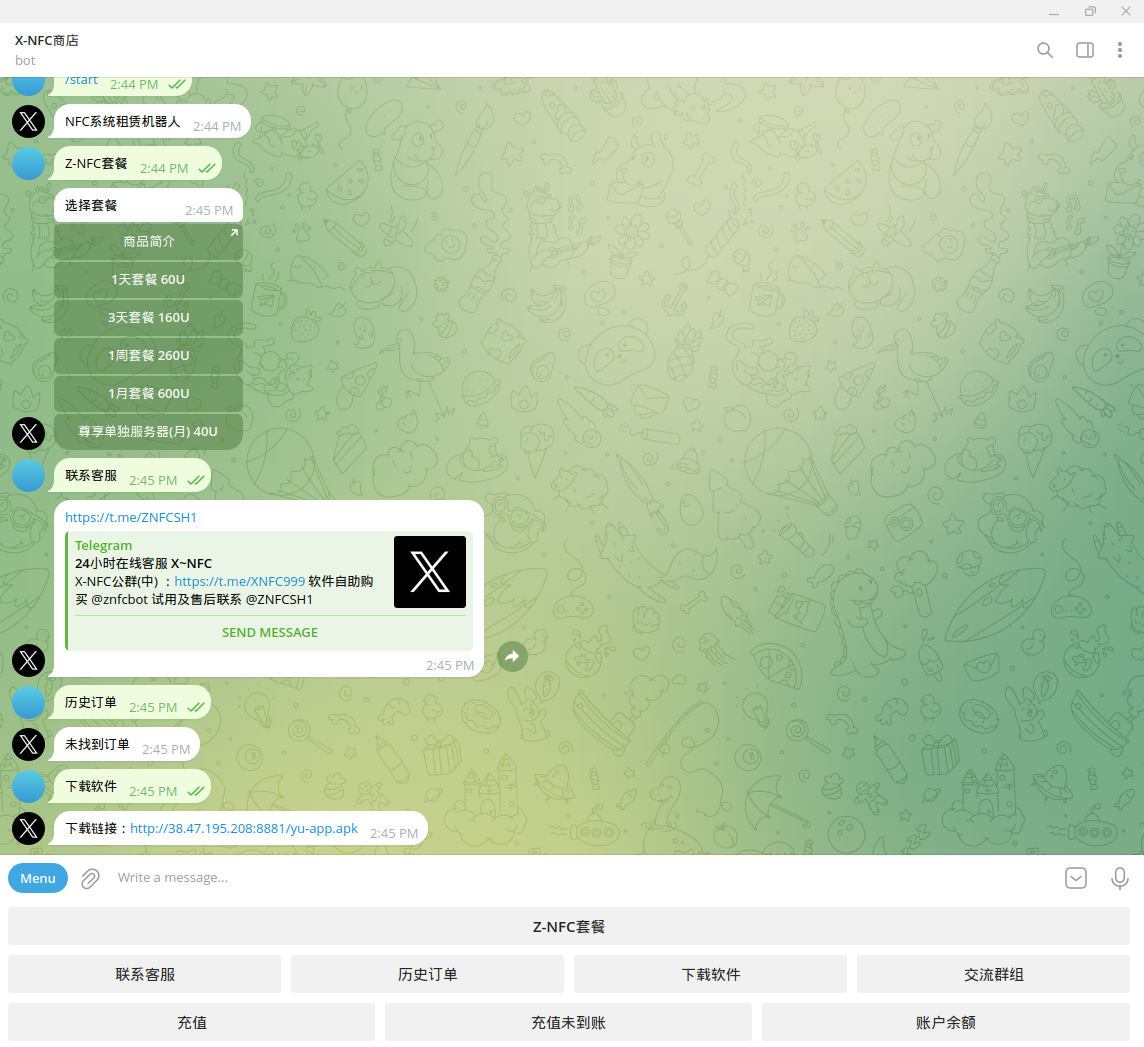
The
identified Telegram channels provide detailed manuals on how to use
Z-NFC for fraud. The bad actors created intuitive videos guiding
cybercriminals on defrauding consumers and using compromised payment
data via NFC.
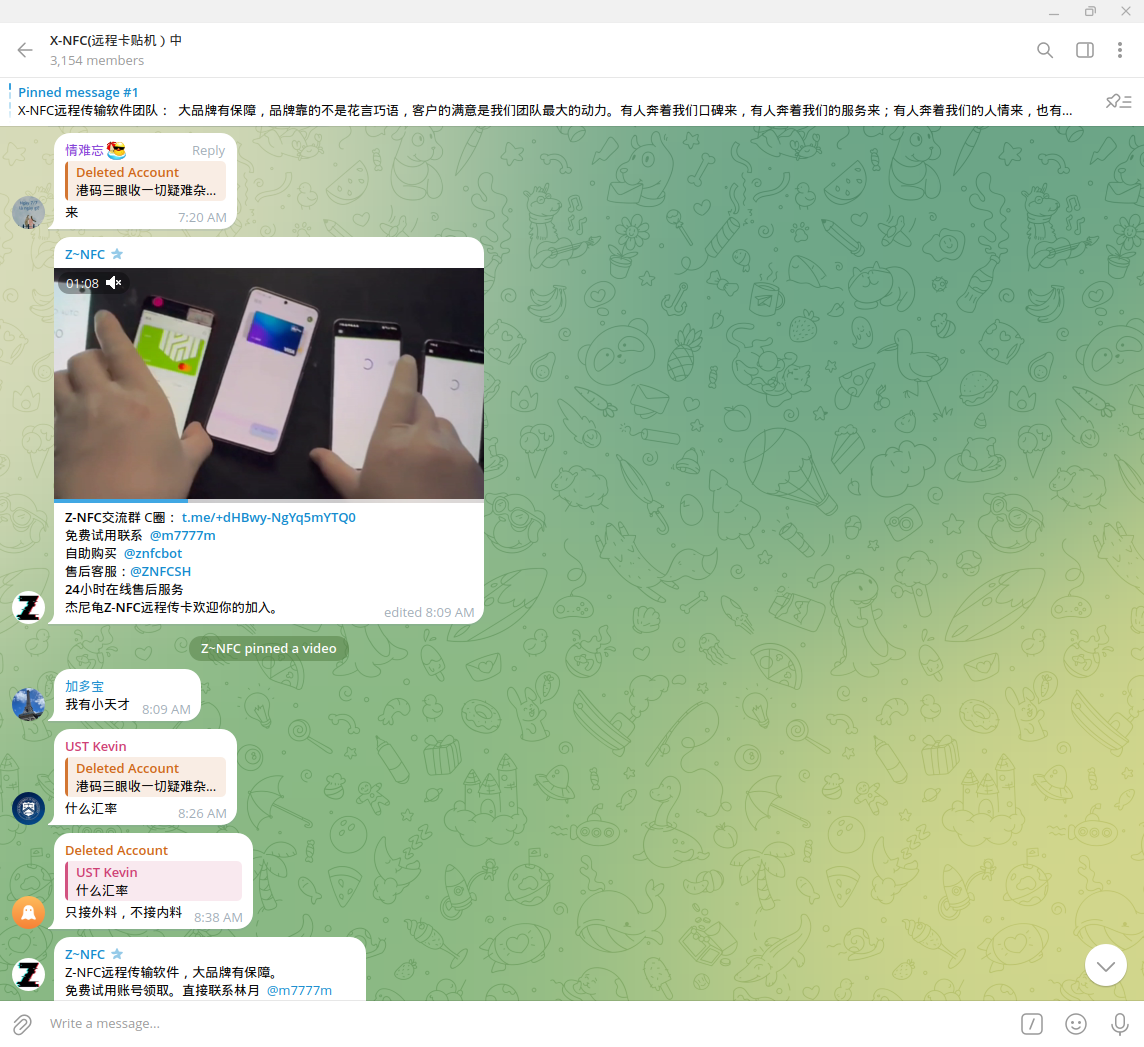
Most of the manuals are written in Chinese. This detail may highlight that the tools are primarily developed by Chinese cybercriminals for their associates who are also based in China due to trust concerns. The actors are more comfortable working with each other because they reside in China, owing to security and ideological factors, as well as an established hierarchy in the underground community that allows them to vet each other more quickly compared to foreigners.
Multiple Chinese-speaking cybercriminal channels dedicated to carding have been identified on Telegram, with some having over 5,946 active members.
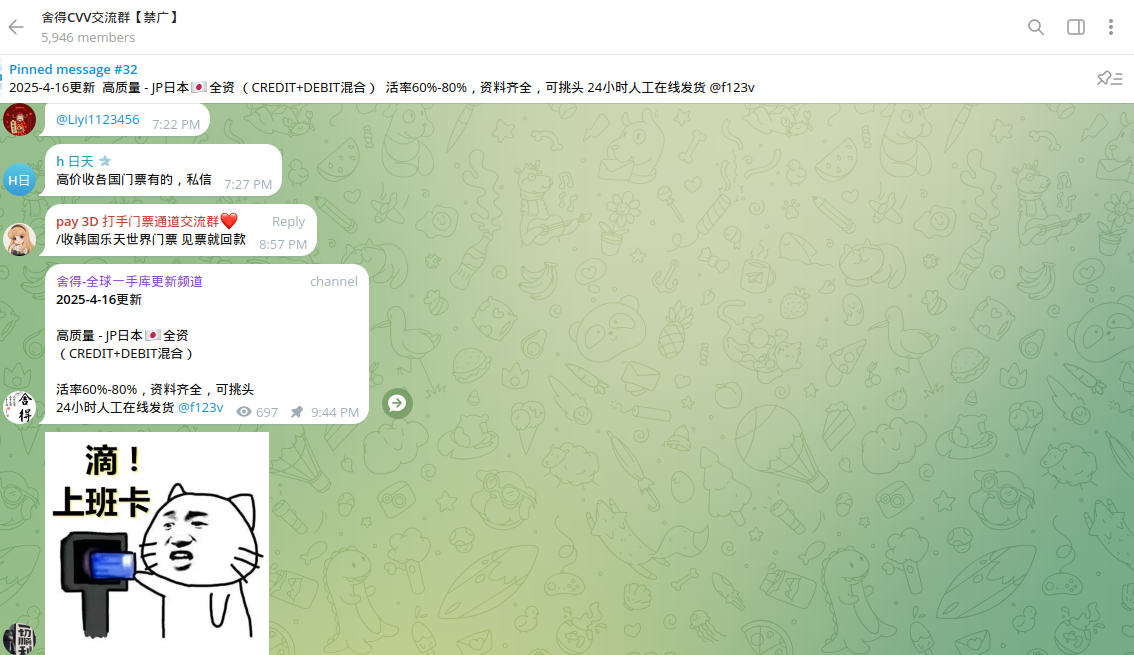
Based on the analysis of the posts, Chinese cybercriminals target the US, Australia, Canada, Japan, the UK, Malaysia, and Taiwan, along with African countries, as their main priority for conducting fraud.
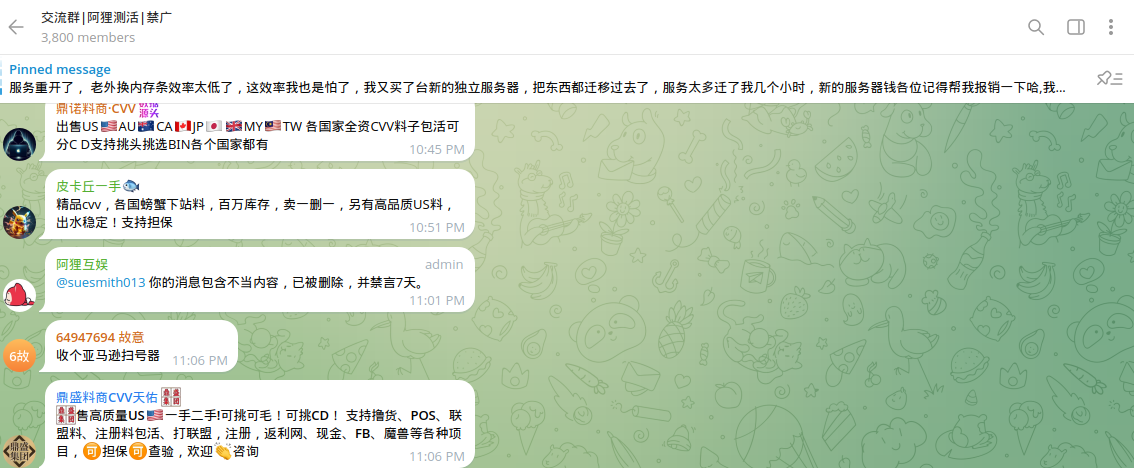
The UAE has also been identified as one of the countries frequently targeted by Chinese cybercriminals focused on payment fraud:
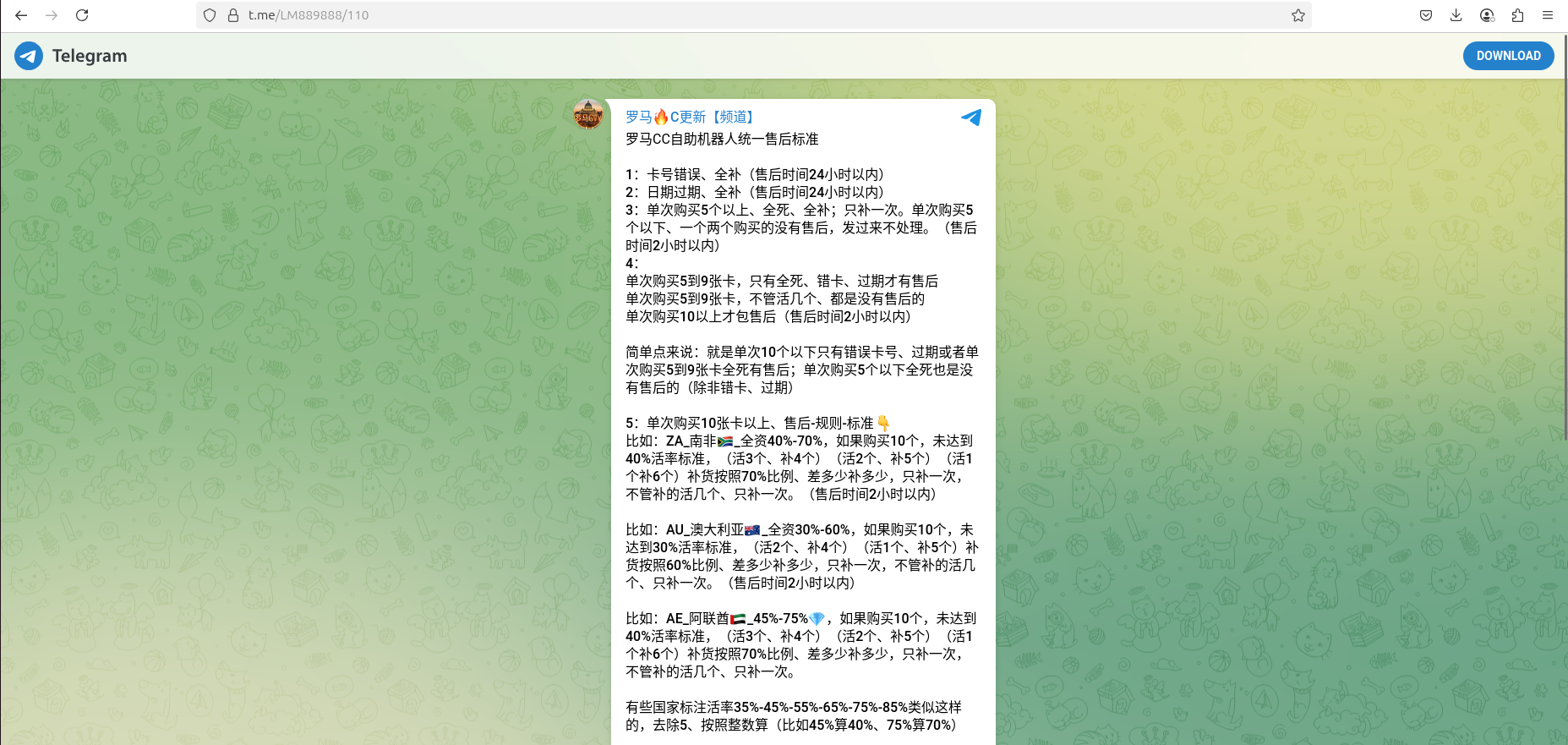
Resecurity has identified several cybercriminal groups targeting financial institutions and their customers in the UAE and other countries of the GCC .
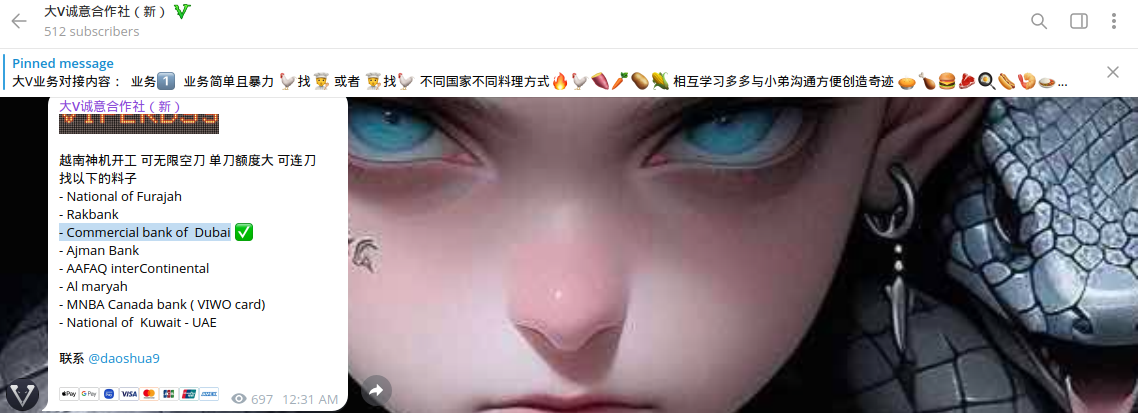
Cybercriminals are increasingly targeting consumers in the UAE and GCC for several reasons, primarily linked to the region's economic landscape, digital transformation, and the high value of personal data. The region boasts a high per capita income, making residents and tourists attractive targets for cybercriminals.
The financial sector in the Kingdom of Saudi Arabia is particularly attractive to cybercriminals due to the high value of financial data and the frequency of online transactions. For instance, Resecurity identified several Chinese underground vendors focusing specifically on compromised payment data belonging to Saudi citizens. NFC technology and contactless payments are gaining significant popularity in the MENA region. These countries have seen rapid adoption of NFC-enabled payments, with Saudi Arabia leading the way with 98% contactless payment adoption for in-person transactions. The MENA region is also experiencing a surge in digital payments, including those facilitated by NFC, that's why financial institutions will be a target of cybercriminal and fraudulent activity.
Z-NFC Application Reverse Engineering
Resecurity acquired the Z-NFC tool and performed reverse engineering on it.
Target
APK:
com.hk.nfc.paypay
Package
Type:
Packed / Encrypted Payload Loader with NFC Emulation
Capabilities
Platform:
Android (HCE-based NFC Emulation)
Protection:
Uses native libraries (libjiagu.so, libjgdtc.so) and runtime
obfuscation
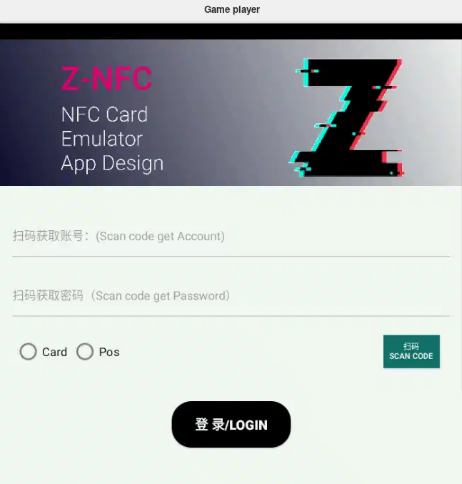
The Z-NFC Card Emulator is an NFC card emulator that leverages Android’s Host Card Emulation (HCE) capabilities. The application is heavily obfuscated and employs native libraries to conceal its true purpose. It operates as a loader shell, decrypting and dynamically loading secondary payloads during runtime. Designed to emulate NFC cards through HCE, the application enables unauthorized access to contactless systems, including payment terminals and credit card infrastructure.
Application Structure
- Primary Package: com.stub.StubApp
- Launch Point: Dynamically replaced Application class at runtime
Permissions:
- NFC (required for Host Card Emulation)
- Internet (C2 comms)
- Camera, Storage, Network State
Native Libraries:
- libjiagu.so or custom variants
- Custom payload loader: libjgdtc.so
The application is initially delivered as a standard Android APK with the package name com.hk.nfc.paypay. On the surface, it appears to be a legitimate NFC utility, featuring a minimal and generic interface centered around a login screen (com.hk.nfc.paypay.gui.LoginActivity). However, beneath this simplistic façade, the app employs several stealth mechanisms designed to obscure its true purpose and functionality.
-
Stub
Architecture:
The APK uses a stub-based loading structure, with com.stub.StubApp acting as a wrapper rather than the true application logic. This stub is responsible for initializing the environment and acting as a shell that prepares the real (hidden) application for execution.
- Obfuscated
Payload Location:
The actual malicious payload is not part of the visible Java code. Instead, it is:- Packed inside encrypted native .so libraries (e.g., libjiagu_64.so) located under the app’s private /data/data/<package>/.jiagu/ directory.
- Embedded within the assets folder, though extracted only when necessary.
- Dynamic
Application Injection:
At runtime, the stub uses native bridging and Java reflection to:- Dynamically decrypt and load a hidden class (entryRunApplication)
- Replace itself with the real Application instance using methods like attach() and native loaders (interface7, interface21).
- Dynamic
Extraction:
Before loading, the app verifies if the encrypted native payload needs to be updated. It uses a file comparison mechanism (via BufferedInputStream) to check whether the encrypted .so files differ from existing ones. If so, it writes the correct version to disk.
This multi-layered initialization allows the app to evade static analysis and delay execution of malicious components until runtime, effectively hiding the bulk of its behavior from traditional analysis tools.
Execution and Encryption Process details
The app sets up the execution environment, loads encrypted native libraries, and dynamically replaces the visible application with the real one at runtime.
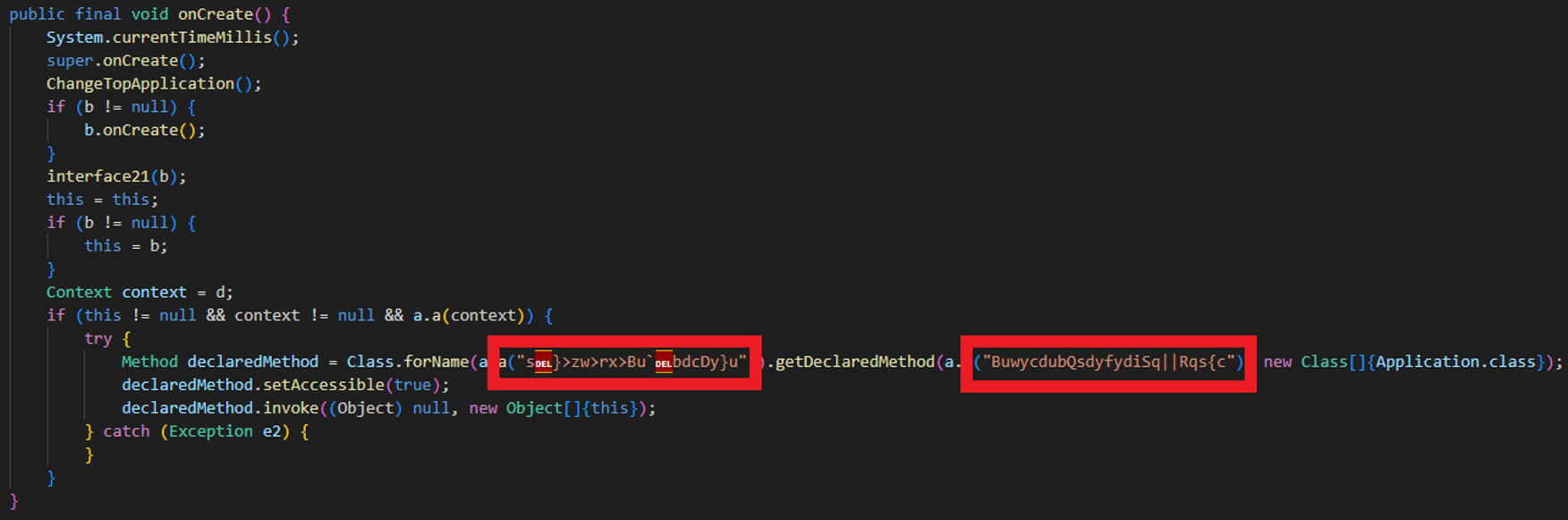
The app targets Android 9 specifically to bypass reflection restrictions by accessing and modifying internal system fields. Class names, method identifiers, and package references are obfuscated using a simple XOR cipher (^ 0x10), making automated decompilation output hard to interpret.
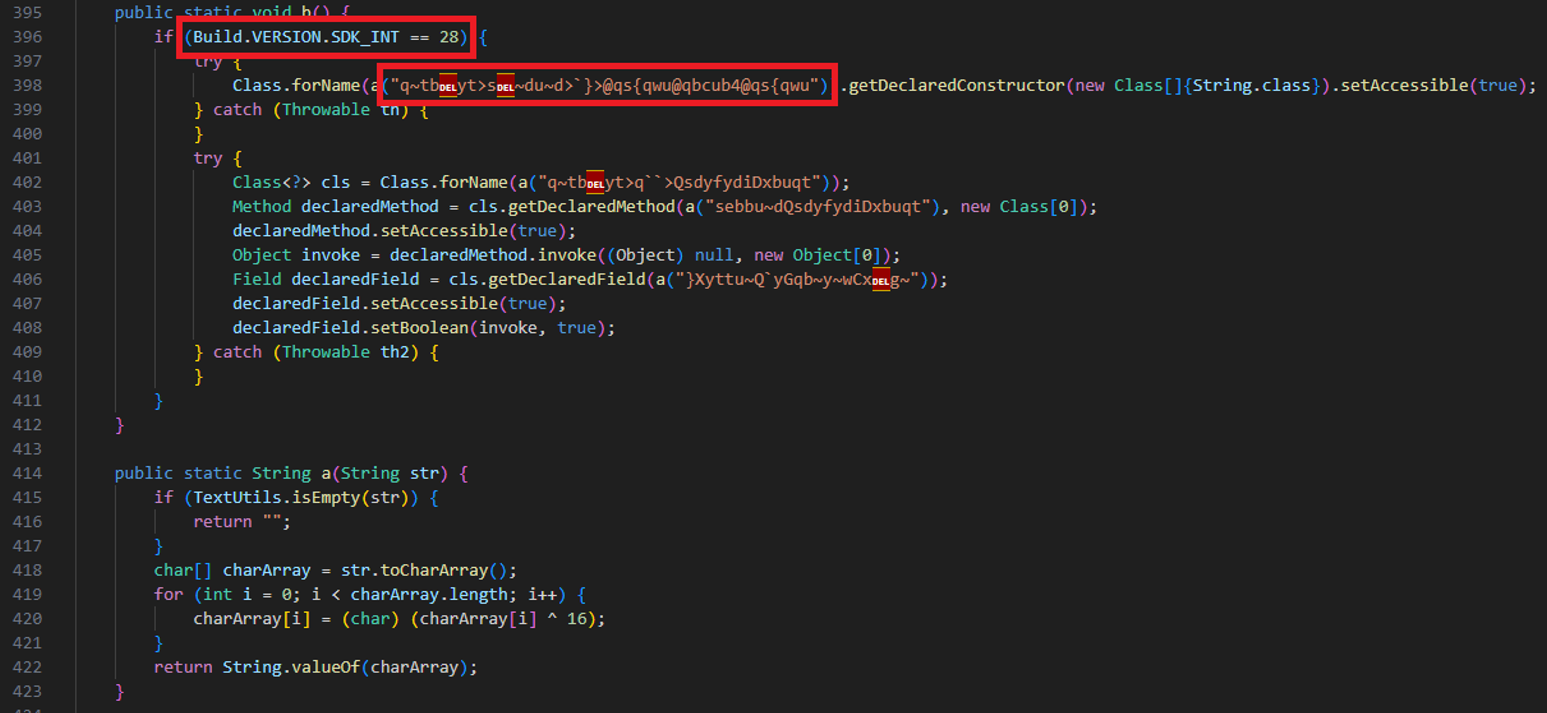
The app verifies its runtime environment by comparing the actual package name against the expected one. If the check fails, it likely prevents execution to avoid analysis or tampering.
The Malicious payloads are stored in native .so libraries (e.g., libjiagu_64.so) located in the app's private data directory (/data/data/<package>/.jiagu/). These payloads are loaded and invoked using native methods such as interface7() and interface21(), keeping critical logic outside the Java layer.
The payload injection and execution are performed via JNI + reflection, allowing evasion from static scanners.
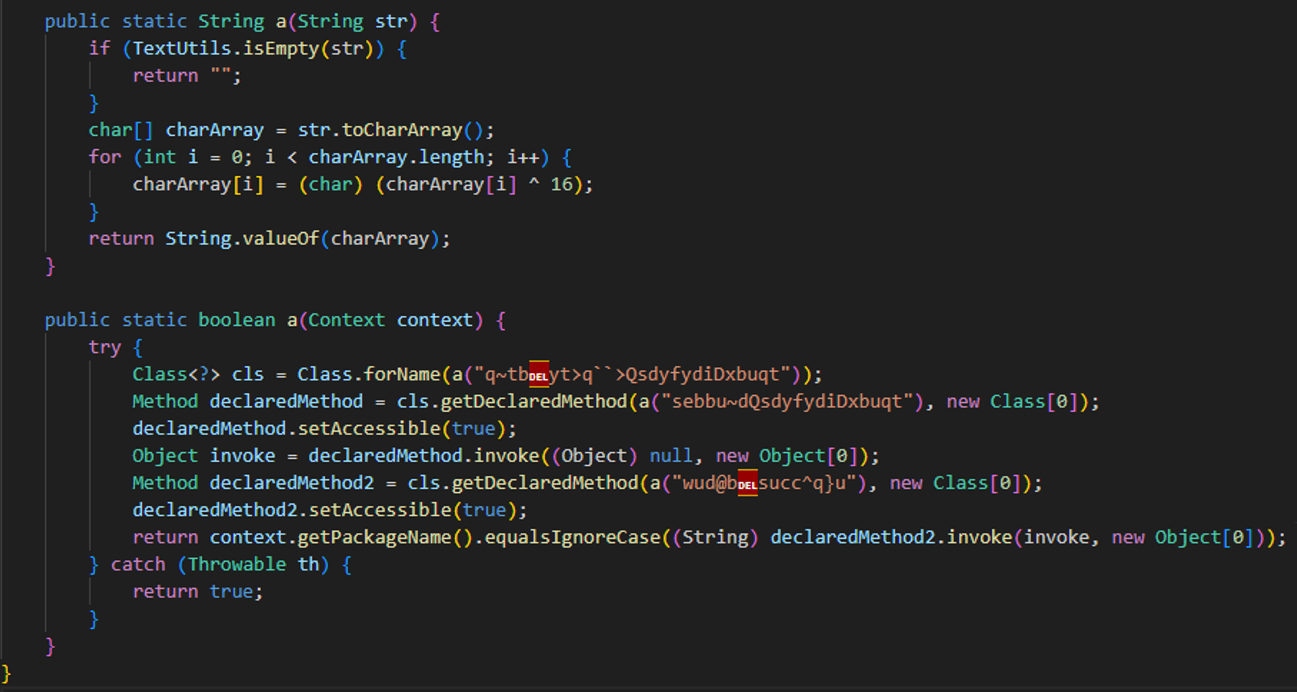
If we decode the obfuscated strings (like q~tbyt>q``>QsdyfydiDxbuqt), they point to this string:
- android.app.ActivityThread
The app utilizes Host Card Emulation (HCE) to mimic a physical ISO 14443 NFC smart card by registering a service that extends HostApduService. This allows it to respond to APDU command sequences just like a real card would. The payloads it handles are likely customizable, enabling users to define specific NFC responses — a capability that could potentially be used to spoof identity-based card systems.
When NFC-based identity systems can be spoofed, the consequences could be severe across sectors relying on contactless authentication, such as physical or digital access control, payments, and transit systems. Attackers could clone or emulate legitimate credentials, gaining unauthorized access to secure locations, conducting fraudulent transactions, or impersonating individuals for malicious purposes. This undermines trust in digital identity infrastructures and could lead to financial losses, physical breaches, data breaches, and safety concerns, particularly in high-security environments like corporate offices, healthcare facilities, or government installations. Furthermore, widespread spoofing could delay the broader adoption of mobile ID technologies, prompting stricter regulatory scrutiny and costly upgrades to more secure authentication.
Google Play enforces strict security and policy requirements for Android apps utilizing Host Card Emulation (HCE) technology, which allows devices to emulate smart cards for contactless transactions. Apps that leverage HCE for payments or other sensitive use cases must comply with Google’s security standards. Apps that fail to meet these requirements or misuse NFC capabilities risk being removed from the Play Store. However, these apps are available outside of Google Play and side-loaded, which is how they bypass all Android restrictions and can be used maliciously.
The app utilizes Host Card Emulation (HCE) to mimic a physical ISO 14443 NFC smart card by registering a service that extends HostApduService. This allows it to respond to APDU command sequences like an actual card. The payloads it handles are likely customizable, enabling users to define specific NFC responses — a capability that could be used to spoof identity-based card systems.
Indicators of Compromise (IOC)
Indicator |
Description |
Package Name |
com.hk.nfc.paypay |
App Name |
Often disguised as utility/NFC tool |
Native Libs |
libjiagu.so, libjgdtc.so |
Path |
/data/data/<pkg>/.jiagu/libjiagu_64.so |
Class |
com.stub.StubApp |
Suspicious String |
"entryRunApplication" – real app class |
Permissions |
NFC, Camera, Internet, Storage access |
The
reverse engineering identified a CN-based network host likely used as
a server for license activation.
URL: https://znfcqwe.top
MD5: 844ef02b3ac1c81342fe2f0afa9092d7
SHA-1: c0850367cf4bfb038aaa332685f73ac3d1e9ad10
SHA-256: 1663a67a95612552caf850604657ddc508161a1fb2a25144abffec8c5213a77b
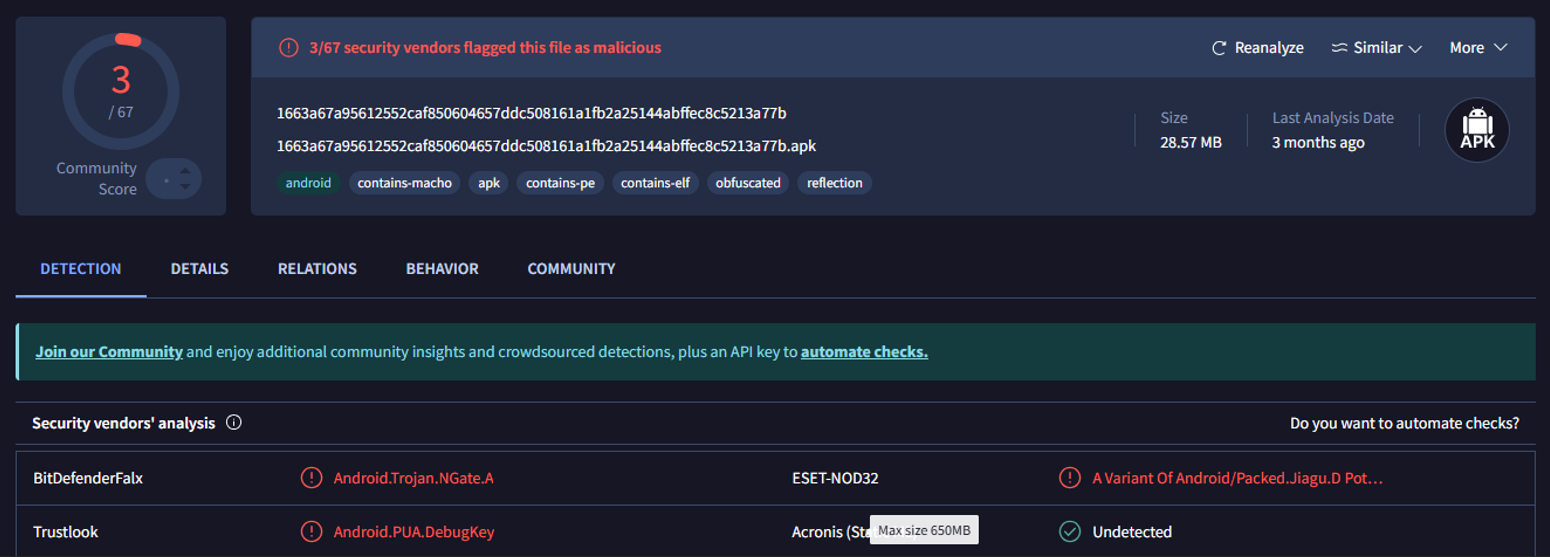
The Z-NFC behaves like a malware loader, using advanced Android packing, native code injection, and NFC emulation to conceal and execute payloads. It’s likely part of a broader NFC-based testing or exploitation toolset. The ability to emulate NFC cards dynamically may enable physical security bypass or unauthorized access in real-world environments.
NFC-enabled POS Terminals - for Sale on the Dark Web
Why is NFC-enabled fraud still possible? Traditional payments typically require some Cardholder Verification Method (CVM) such as PIN or signature. For low-value contactless payments below the “Contactless CVM limit,” no CVM is required—the consumer can simply Tap & Go. Note that the Contactless CVM limit varies from country to country. Besides traditional POS terminals, cybercriminals also abuse tap on phone smart software solutions (sometimes called Soft POS) that turns NFC-enabled Android smartphones, tablets and other handheld devices into payment terminals.
Cardholder verification is required for contactless card transactions above the CVM limit (e.g., by online PIN using the merchant PIN pad or signature). The merchant is liable for contactless transactions above the CVM limit that have no cardholder verification. Unfortunately, cybercriminals actively exploit this issue by executing multiple small transactions while leveraging a high volume of compromised cards.
Resecurity identified multiple Chinese cybercriminal groups offering NFC-enabled POS terminals to facilitate fraudulent transactions and money laundering operations. The bad actors register these terminals with money mules, creating merchant accounts in various processing systems and financial institutions globally. Such fraudulent merchants have been identified in China, Malaysia, Nigeria, and South Africa.

Typically, these merchants have a daily limit, so cybercriminals are always looking for new ways to scale their operations by adding new money mules who can open accounts for a commission.
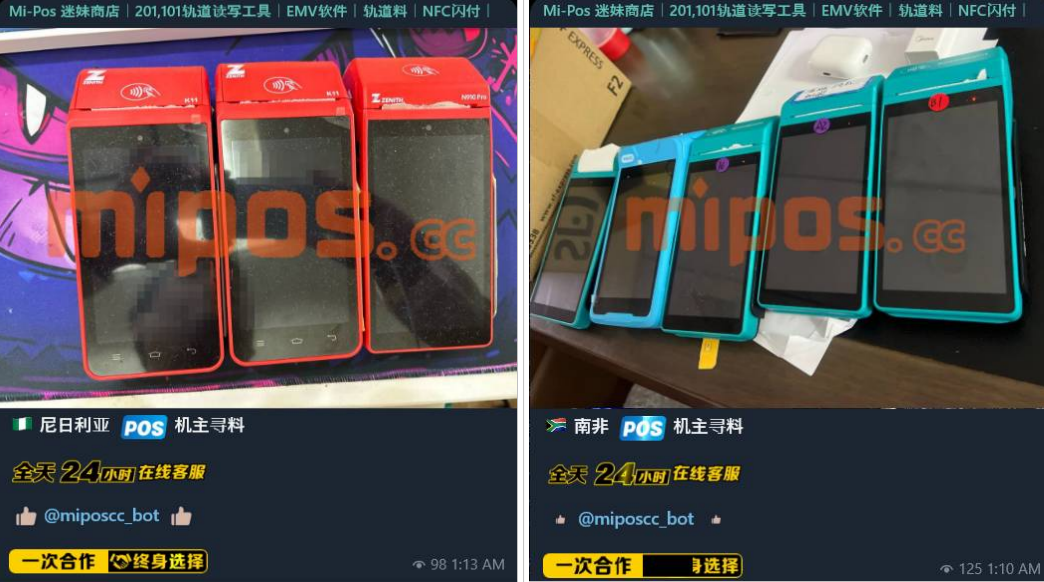
Using stolen compromised payment data, Chinese cybercriminals automate transactions using tools like Z-NFC and NFC-enabled POS terminals, which are typically placed right in front of them.
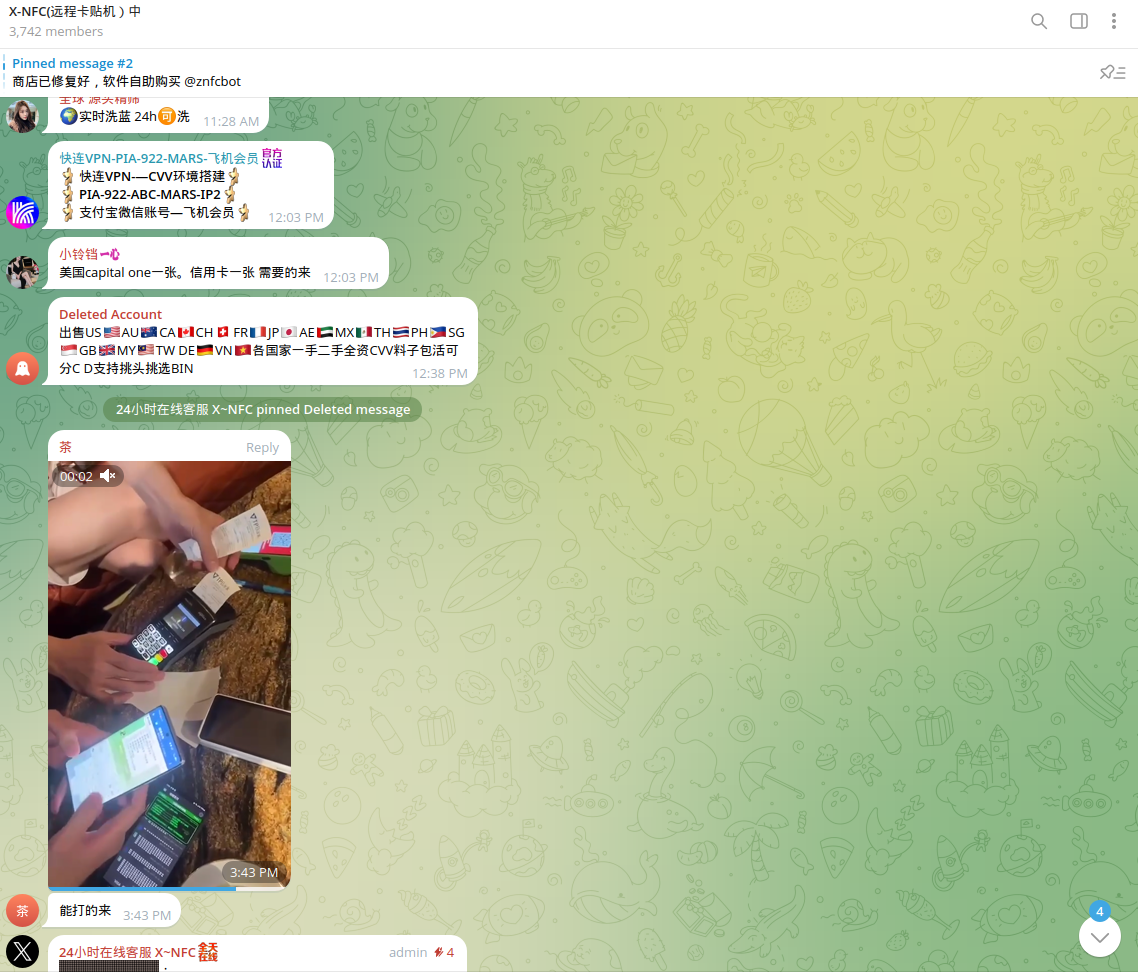
Cybercriminals sometimes abuse existing NFC-enabled POS terminals installed by legitimate businesses. This is typically done by insiders or dishonest sellers who use their businesses for money laundering—'double dipping' from both sides: their own business and cybercrime. Notably, such merchants are valuable to cybercriminals because they already have an established track record and history of legitimate customer transactions. As a result, it may take time to detect fraud involving them, and the seller may act as if they do not know anything about it.
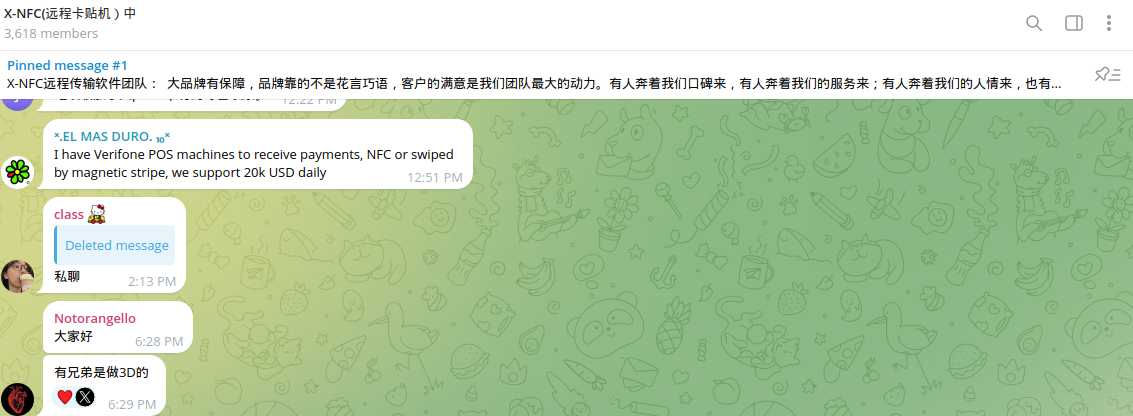
So-called "grey" merchants with NFC-enabled POS terminals are in high demand on the Dark Web. Chinese cybercriminals are looking for associates who will provide these terminals for cybercriminal purposes in different countries.
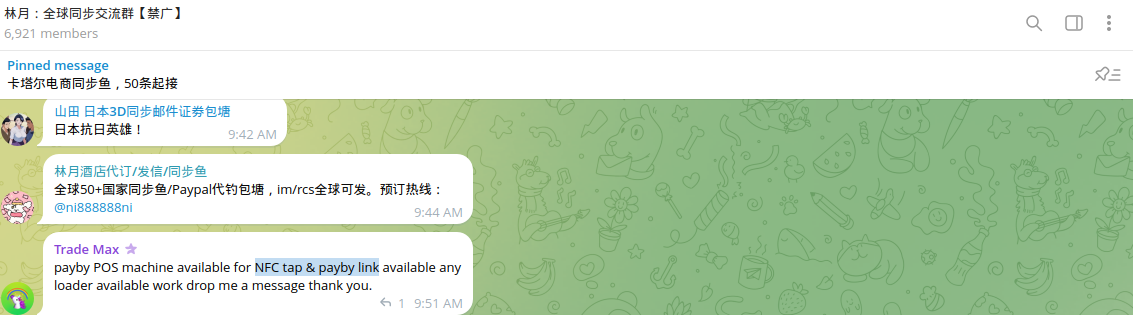
In addition, various cybercriminal channels have been identified that offer equipment to orchestrate fraud via NFC, including NFC readers, compatible cards (white plastic), encoders, and other devices.
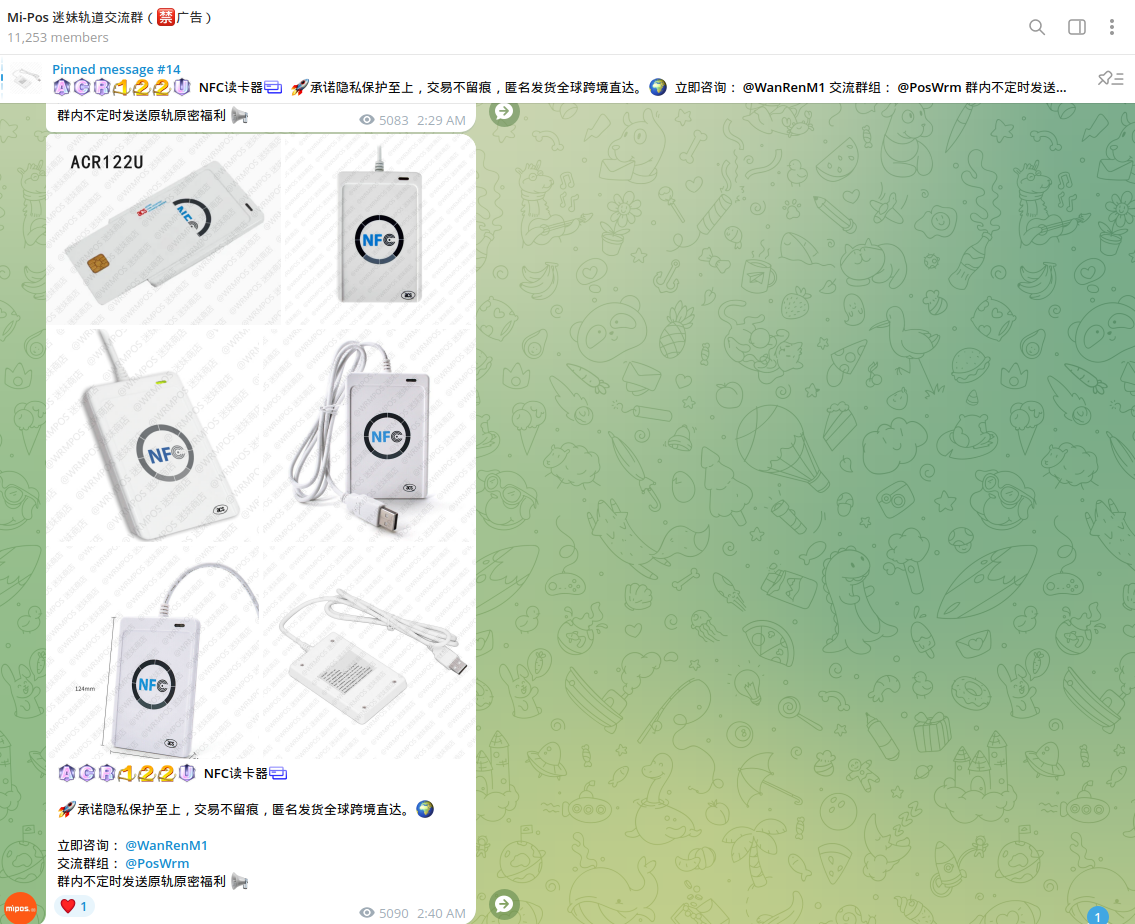
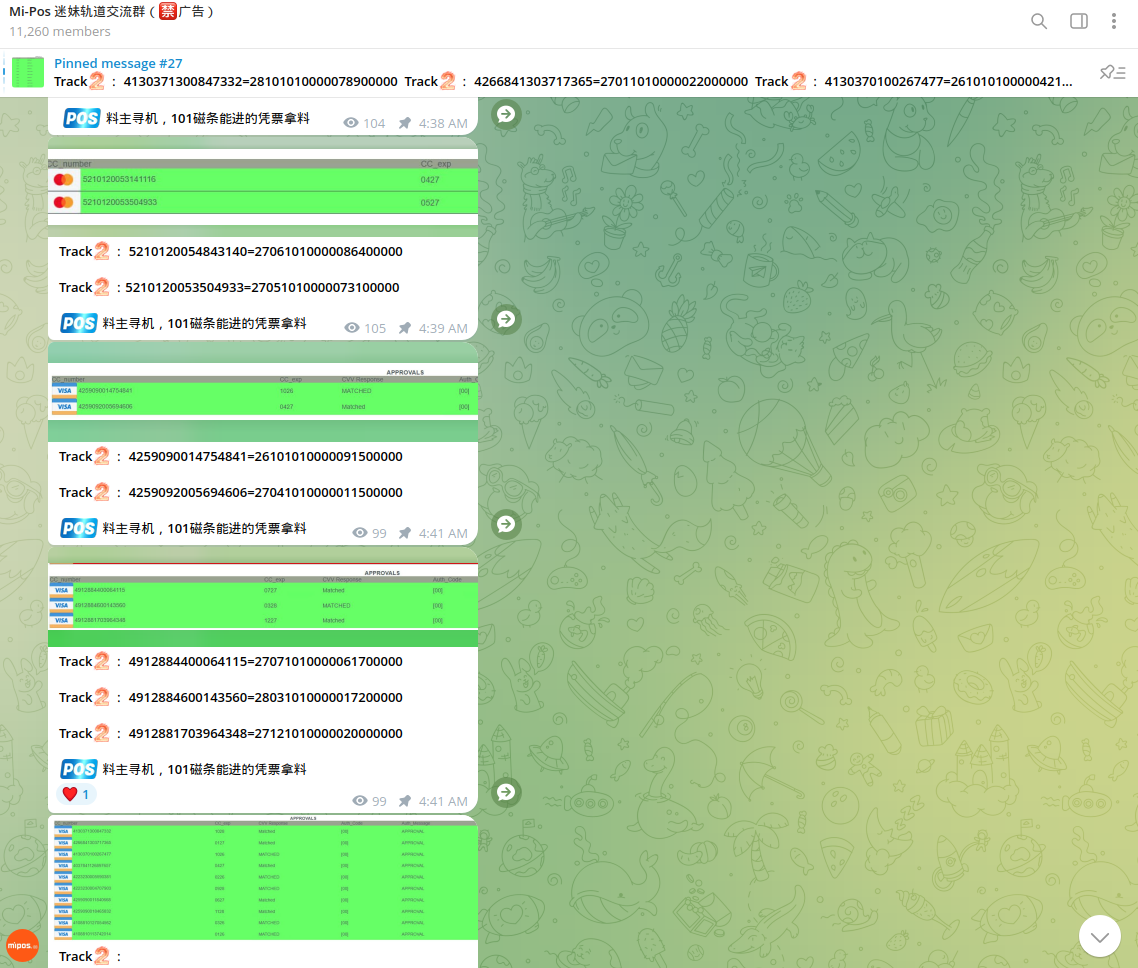
Cybercriminals use stolen Track 2 data, which is intercepted by ATM skimmers or acquired on the Dark Web, to record it on 'white plastic' and then use it on POS terminals.
On the same Telegram channel, they share samples of Track 2 data, exchanging experience and successful fraudulent operations.
Cybercriminals also sell e-SIM contracts to activate the Internet on POS terminals and communicate with payment gateways. These contracts can be activated by money mules or registered under fake details. Some of the e-SIM offerings have been observed to originate from Hong Kong, Japan, and the United States.
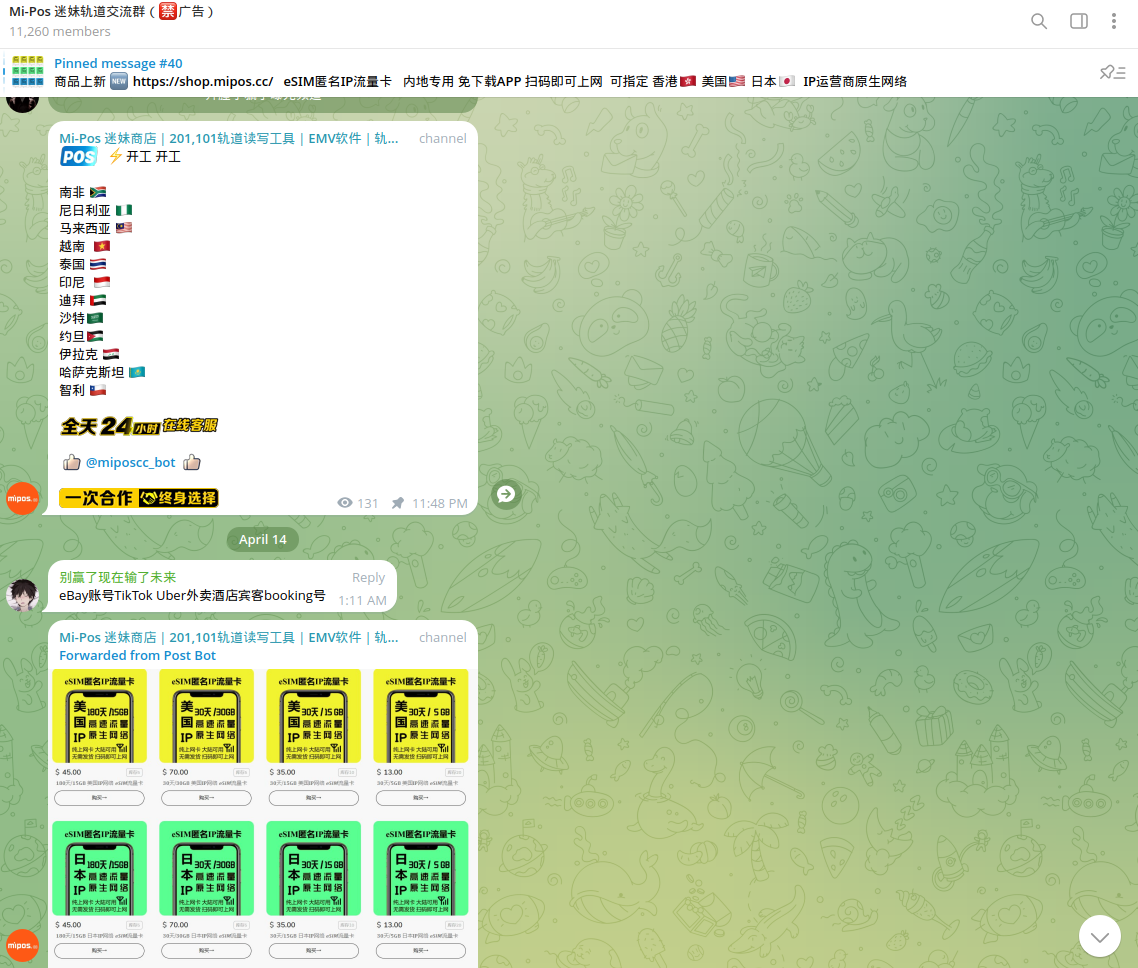
An e-SIM allows users to quickly switch between operators without needing a physical SIM card or a traditional internet connection, making cybercriminal operations extremely mobile.
Loyalty Points Fraud
NFC technology significantly enhances loyalty programs for businesses and consumers. NFC enables contactless transactions, allowing customers to earn and redeem loyalty points quickly and conveniently. By tapping their NFC-enabled device or card at a point-of-sale terminal, customers can automatically register their purchases and accumulate points without needing physical loyalty cards or following lengthy processes.
In our exploration, Resecurity discovered a significant gap in the security of loyalty points programs in the context of NFC fraud. Loyalty points fraud revolves around the unauthorized acquisition, transfer, or redemption of loyalty points. These points, accumulated through customer engagement with various programs, often hold substantial monetary value, making them attractive to cybercriminals. Like credit card fraud with Google and Apple Wallet, once loyalty cards are present on the device, fraudsters can use them for fraudulent purposes.

X-NFC customers are widely using this approach to defraud consumers of airlines, hotels, gas (petro) loyalty programs and steal their points.
Significance
NFC (Near Field Communication) fraud is a growing concern due to the increasing adoption of NFC technology in mobile payments, identity verification, and other contactless applications. The rise of contactless payments, especially during the COVID-19 pandemic, has significantly increased the volume of NFC transactions. This growth has created more opportunities for fraudsters to exploit the technology. As the market for contactless payments continues to expand, so does the potential for NFC-related fraud. NFC is also used for identity verification, making it a target for identity theft.
Cybercriminals can exploit NFC vulnerabilities to access personal information stored on devices or NFC-enabled ID cards, leading to further misuse of the victim's identity. NFC fraud can result in significant financial losses, especially when attacks are scaled. For example, the "Ghost Tap" attack allows cybercriminals to relay stolen NFC payment data to make unauthorized purchases. Even though individual transactions may be small, the cumulative losses can be substantial when applied at scale. Additionally, fraudsters often target resalable goods like gift cards or electronics, further amplifying the financial damage.
Conclusion
Chinese
cybercriminals have become highly active in defrauding consumers
worldwide by exploiting NFC technology and leveraging specialized
tools to abuse NFC-enabled point-of-sale (POS) terminals. Their
tactics involve sophisticated schemes, such as relaying stolen NFC
card data, registering fraudulent POS terminals by money mules, and
conducting large-scale unauthorized transactions. These criminals
exploit the convenience and widespread adoption of NFC technology,
targeting vulnerabilities in payment systems and taking advantage of
poor security measures.
Through advanced tooling and techniques, such as the "Ghost Tap" method and remote transaction relays, they can bypass detection systems and cause significant financial damage to victims. The global nature of NFC payments and the anonymity provided by money mules and encrypted communication channels make these fraud operations challenging to track and shut down.
The growing prevalence of NFC in everyday transactions underscores the urgent need for stronger security measures, enhanced fraud detection systems, and global cooperation to combat this rising threat. Without decisive action, these cybercriminals will continue to exploit NFC technology, posing a serious risk to consumers and businesses worldwide.

